Global Cyber Executive Briefing has been saved
Case studies
Global Cyber Executive Briefing
Insurance
Cyber-attacks in the insurance sector are growing exponentially as insurance companies migrate toward digital channels in an effort to create tighter customer relationships, offer new products and expand their share of customers’ financial portfolios. This shift is driving increased investment in traditional core IT systems (e.g., policy and claims systems) as well as in highly integrated enabling platforms such as agency portals, online policy applications and web- and mobile-based apps for filing claims. Although these digital investments provide new strategic capabilities, they also introduce new cyber-risks and attack vectors to organizations that are relatively inexperienced at dealing with the challenges of an omni-channel environment. What’s more, the challenges are likely to become more complex as insurers embrace big data and advanced analytics that require collecting and handling vast amounts of consumer information. As insurers find new and innovative ways to analyze data, they must also find ways to secure the data from cyber-attacks.
Explore Content
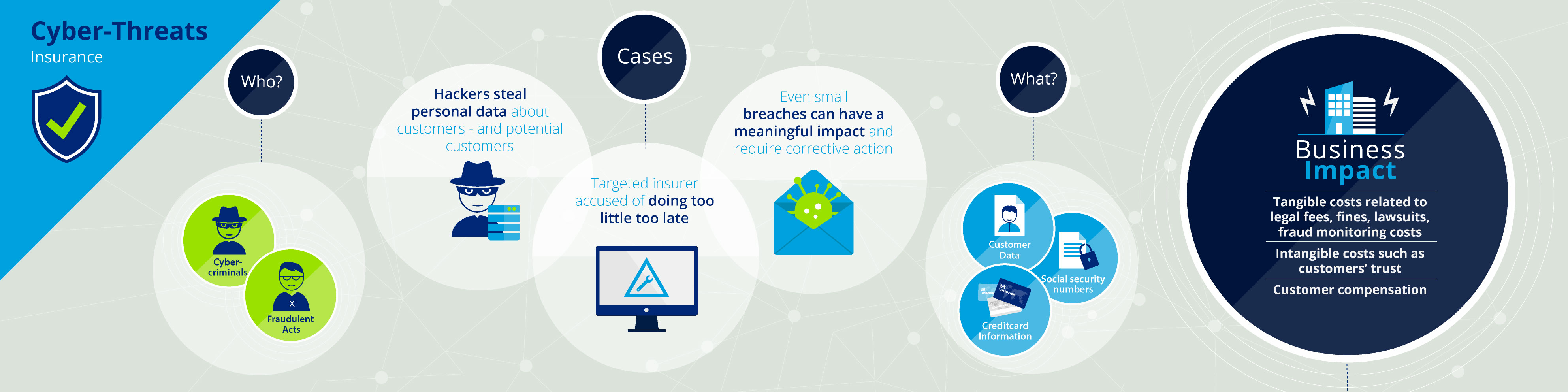
- Case - 1: Hackers steal personal data about customers -- and potential customers
- Case - 2: Even small breaches can have a meaningful impact and require corrective action
- Case - 3: Targeted insurer accused of doing too little too late
Cyber-criminals have started to recognize that insurers possess large amounts of personal information about their customers, which is very attractive to identity thieves and fraudsters. In some cases, insurers also possess significant amounts of customer credit card and payment data. However, there is at least one case in the insurance sector where the victims of a cyber-attack weren’t even paying customers but merely consumers who had requested a price quote (case #1).
Cyber-criminals targeting insurers often have significant resources. This enables them to employ sophisticated attacks that combine advanced malware with other techniques such as social engineering (case #2).
Attacks on insurance firms can result in significant, tangible damages such as fines, legal fees, lawsuits and fraud monitoring costs. However, a less obvious but no less significant impact may be loss of trust, driven by customers’ concerns about whether their information is truly safe (case #3). Since the insurance business revolves around trust, a major breach can have a very real impact on an insurer’s brand and market value.
It’s worth noting that most of the breaches publicly reported by insurance companies to date have been characterized as short term attacks, with cyber-criminals compromising a system, stealing specific information and then quickly moving on. In fact, our research did not uncover any documented cases of long-term infiltration and cyber-crime in the insurance sector. However, we believe the number of long-term attacks may be silently growing as attackers quietly slip in undetected and establish a persistent, ongoing presence in critical IT environments.
Over the years, many insurance organizations have invested a lot of money in security tools and processes that may be providing a false sense of security. As attackers learn to leverage encryption and other advanced attack techniques, traditional tools such as firewalls, antivirus software, intrusion detection systems (IDS) and intrusion preven¬tion systems (IPS) are becoming less and less effective. As a result, many insurers may be misallocating their limited resources to address compliance-oriented, easily recognized threats while completely overlooking stealthy long-term threats that ultimately could be far more damaging.
Hackers steal personal data about customers -- and potential customers
Organization
A group of large insurance and financial services companies.
Scenario
Cyber-criminals breached the company database and stole information of more than one million customers and sales prospects, including driver’s license data and social security numbers.
Attackers and motivation
Cyber-criminals were after personal identifiable information in order to sell it on the black market for identity fraud purposes.
Techniques used
Part of the network used by the organization’s members was breached by cyber-criminals and used to steal customer information.
Business impact
The organization was obliged to provide affected customers with free credit monitoring for a year, and to reimburse all damages resulting from the breach. In addition to those tangible costs – which were substantial -- the organization suffered significant brand damage and loss of trust.
Case 1
Even small breaches can have a meaningful impact and require corrective action
Organization
A very large investment and insurance company.
Scenario
The attack targeted company employees with e-mails containing malware that could capture confidential data such as bank account numbers, social security numbers, user accounts/logins, passwords and credit card numbers. Hackers used this information to compromise several servers, including servers used by employees to remotely access the company’s IT systems.
Attackers and motivation
Cyber-criminals were after online banking information to perpetrate fraud for financial gain.
Techniques used
The attack targeted company employees with e-mails containing malicious software that could capture confidential data such as bank account numbers, social security numbers, user accounts/ logins, passwords and credit card numbers.
Business impact
Although the attack affected only a small number of employees -- and only a handful of customers -- it still received media coverage that damaged the company’s reputation.
Case 2
Targeted insurer accused of doing too little too late
Organization
An insurance and financial services firm that specializes in serving seniors.
Scenario
Attackers exploited vulnerable software on the company’s servers and stole payment card information for more than 93,000 customers, including names, addresses and unencrypted card security codes.
Attackers and motivation
Cyber-criminals were after payment card information to sell on the black market and commit fraudulent transactions.
Techniques used
Vulnerabilities in the company’s systems and software were discovered and exploited by the cybercriminals to gain access to payment card information.
Business impact
The company immediately removed the vulnerable IT elements and had to issue a formal apology. It also offered free identify fraud monitoring to affected customers. However, the company has been strongly criticized for retaining unencrypted security codes --which is a noncompliance issue according to the Payment Card Industry Data Security Standard (PCI DSS) -- and for not reporting the breach to its customers sooner.
Case 3
