Article

CSV Injection in Salesforce
A CSV injection in Salesforce allows malicious users to gain remote control of other computers. By choosing formula code as filename, an attacker can save files with names containing malicious code to the Salesforce platform. Other users might download this data and corrupt their PC by opening it in a tool such as Microsoft Excel. The attacker could gain remote access to the user’s PC.
Background
We discovered a security issue within the CRM platform Salesforce, a software for case management and task management. An attacker can input malicious formula data due to a lack of sufficient input filtering. This allows attacking clients who export the data and open it via tools like Microsoft Excel or LibreOffice. The attacker can now infect users with malware and gain control over their host computers, if the malicious code is executed successfully.
Steps to Reproduce
Upon saving a new file to the platform, a malicious user is able to put formula code into the "filename" field. Afterwards from the Files and Content Management functionality on the platform, all the uploaded files could be downloaded. Other users can export and download the files stored on the platform as a CSV file. If the infected file is opened with Microsoft Excel, the malicious formula code will be executed. In this example, the username "=1+1" was involved in an action. In LibreOffice the formula was interpreted and executed successfully.
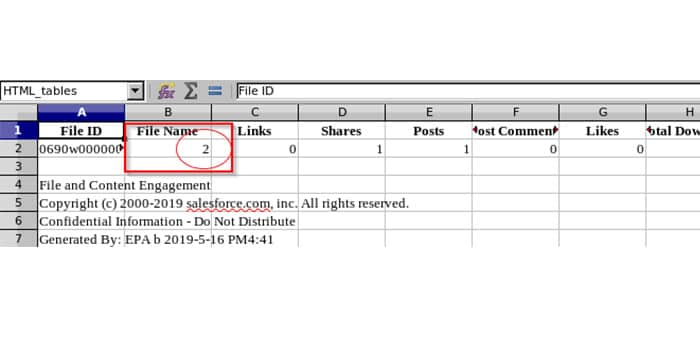
Root Cause
This issue exists due to insufficient input filtering. In order to mitigate the issue, we recommend sanitizing user-supplied input before exporting the data as spreadsheet files on the entire platform.
Fix
The issue is not fixed from Salesforce because they apply risk acceptance.
Credit
Credit for finding and reporting the issue:
Robert Nikolai Reith
Omar Eissa
Evgeni Sabev
Hussam Siraj Cheaib

