Events

ECSAv10 – EC-Council Certified Security Analyst v10
Official EC-COUNCIL Training & Certification
ECSA is a globally respected penetration testing program that covers the testing of modern infrastructures, operating systems, and application environments while teaching the students how to document and prepare professional penetration testing report. This program takes the tools and techniques covered in CEH to next level by utilizing EC-Council’s published penetration testing methodology.
General information
The new ECSAv10 includes updated curricula and an industry recognized comprehensive step-by-step penetration testing methodology. This allows a learner to elevate their ability in applying new skills learned through intensive practical labs and challenges.
Unlike most other pen testing programs that only follow a generic kill chain methodology; the ECSA presents a set of distinguishable comprehensive methodologies that are able to cover different pentesting requirements across different verticals.
It is a highly interactive, comprehensive, standards based, intensive 5-days training program that teaches information security professionals how professional real-life penetration testing are conducted.
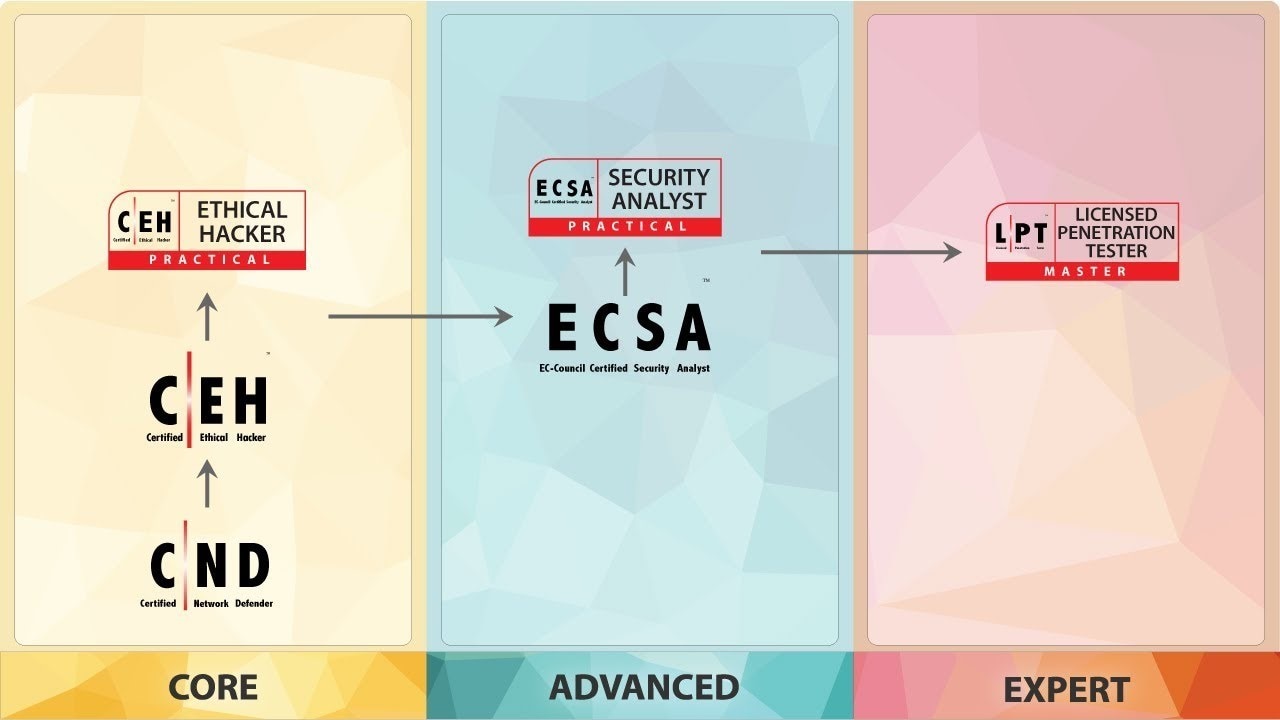
This course is a part of the VAPT (Vulnerability Assessment and Penetration Testing) Track of EC-Council. This is a “Professional” level course, with the Certified Ethical Hacker being the “Core” and the Licensed Penetration Tester being the “Master” level certification.
Deloitte is an official Authorized Training Center for the EC-Council, offering official training sessions, which include:
- Official courseware
- Authorized instructors (with actual professional experience)
- Certification examination voucher
Course outline
ECSAv10 consists of 12 core modules presented during the actual training, and an additional 24 self-study modules to enable continuous learning.
|
Core Modules 1. Introduction to Penetration Testing and Methodologies 2. Penetration Testing Scoping and Engagement Methodology 3. Open Source Intelligence (OSINT) Methodology 4. Social Engineering Penetration Testing 5. Network Penetration Testing Methodology - External 6. Network Penetration Testing Methodology - Internal 7. Network Penetration Testing Methodology - Perimeter Devices 8. Web Application Penetration Testing Methodology 9. Database Penetration Testing Methodology 10. Wireless Penetration Testing Methodology 11. Cloud Penetration Testing Methodology 12. Report Writing and Post Testing Actions |
Self-Study Modules 1. Penetration Testing Essential Concepts 2. Password Cracking Penetration Testing 3. Denial-of-Service Penetration Testing 4. Stolen Laptop, PDAs and Cell Phones 4. Penetration Testing 5. Source Code Penetration Testing 6. Physical Security Penetration Testing 7. Surveillance Camera Penetration Testing 8. VoIP Penetration Testing 9. VPN Penetration Testing 10. Virtual Machine Penetration Testing 11. War Dialing 12. Virus and Trojan Detection 13. Log Management Penetration Testing 14. File Integrity Checking 15. Telecommunication and Broadband 16. Communication Penetration Testing 17. Email Security Penetration Testing 18. Security Patches Penetration Testing 19. Data Leakage Penetration Testing 20. SAP Penetration Testing 21. Standards and Compliance 22. Information System Security Principles 23. Information System Incident Handling and 23. Response 24. Information System Auditing and Certification |
The EC-Council iLabs Cyber Range
The ECSA course is a fully hands-on program with labs and exercises that cover real world scenarios. By practicing the skills that are provided to you in the ECSA class, we are able to bring you up to speed with the skills to uncover the security threats that organizations are vulnerable to.
This can be achieved effectively with the EC-Council iLabs Cyber Range. It allows you to dynamically access a host of Virtual Machines preconfigured with vulnerabilities, exploits, tools, and scripts from anywhere with an internet connection.
Our guided step-by-step labs include exercises with detailed tasks, supporting tools, and additional materials as well as our state-of-the-art “Open Environment” allowing you to launch a complete live range open for any form of hacking or testing.
Target Student
This course will significantly benefit Ethical Hackers, Penetration Testers, Security Analysts, Security Engineers, Network Server Administrators, Firewall Administrators, Security Testers, System Administrators, Risk Assessment Professionals, and anyone who is concerned about the integrity of their network infrastructure.
Prerequisites
Although the prerequisites are not mandatory, it is important to keep in mind that this is an intermediary-level Cyber Security/Penetration Testing course, therefore it will be expected of you to have at least 2 years prior experience in general Cyber Security projects. Also, it is recommended that you prior attend the CEH (Certified Ethical Hacker) course and certification.
Practical information
Ec-Council Certified Security Analyst v10 – Official EC-COUNCIL Training & Certification
Price (VAT excluded): 1.950 EUR / delegate
Dates*:
- August 26 - 30, 2019 | Bucharest
- September 30 - October 4th, 2019 | Bucharest
* Discounts apply for groups of at least 3 participants from the same company.
** The dates are subject to change if the minimum number of participants is not met.
Course language: Romanian (course materials will be in English)
Speaker
Cristian Mocanu - Senior Consultant, Deloitte Romania
Cristian is an Instructor and Senior Consultant at Deloitte Risk Advisory, with over 10 years experience in IT, including 8 in IT security. Having a large experience in a governmental authority, in the Telecommunications field, as a Network Security Administrator, he managed a big infrastructure spanning the country, being involved in various infrastructure and security projects. He is currently part of the local Deloitte Penetration Testing and Ethical Hacking team, handling complex Penetration Testing engagements in industries such as Financial, Education, Manufacturing, Telecommunications.
Cristian holds the following certifications:
EC-Council Certified Instructor (CEI), EC-Council Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA), EC-Council Licensed Penetration Tester (LPT), Offensive Security Certified Professional (OSCP), Offensive Security Certified Expert (OSCE), Red Hat Certified System Administrator (RHCSA), Red Hat Certified Engineer (RHCE), Red Hat Certificate of Expertise in High Availability Clustering (RH EX436).

All the participants will be receiving:
• Official EC-Council Courseware
• Official EC-Council iLabs Cyber Range access for 6 months
• Official EC-Council ECSA Certification Examination voucher
For more information regarding our courses, please feel free to get in touch with us.
Adrian Bucur | Deloitte Academy
Mobil: +40 756 096 353
E-mail: adbucur@deloitece.com
Subscribe here to be notified about Deloitte Romania events and publications of your choice.