The Past and Future of Red Teaming Bookmark has been added
With ever increasing sophisticated cyber security crime cases, it is essential for organizations to strength their defense capabilities and proactively identify vulnerabilities.
Red teaming, often referred to as "ethical hacking" is a proactive approach that has been increasingly adopted in the corporate organizations in recent years in Japan and oversea.
This article overviews the evolution of red teaming and the recent trend that are likely shape the future of red teaming.
The Evolution of Red Teaming
The original of red teaming traces in the military sector, where it was a way to assess the effectiveness of security measures by using an external perspective. Over time, the concept expanded to the cyber security training exercise used by the organizations like critical infrastructure, financial institutions, and other corporate environments of various industries.
At the beginning, red teaming exercises were mostly penetration testing and vulnerability assessments. However, as the digitalization advanced and cyber-attacks become more sophisticated, red teaming exercises expanded its scope.
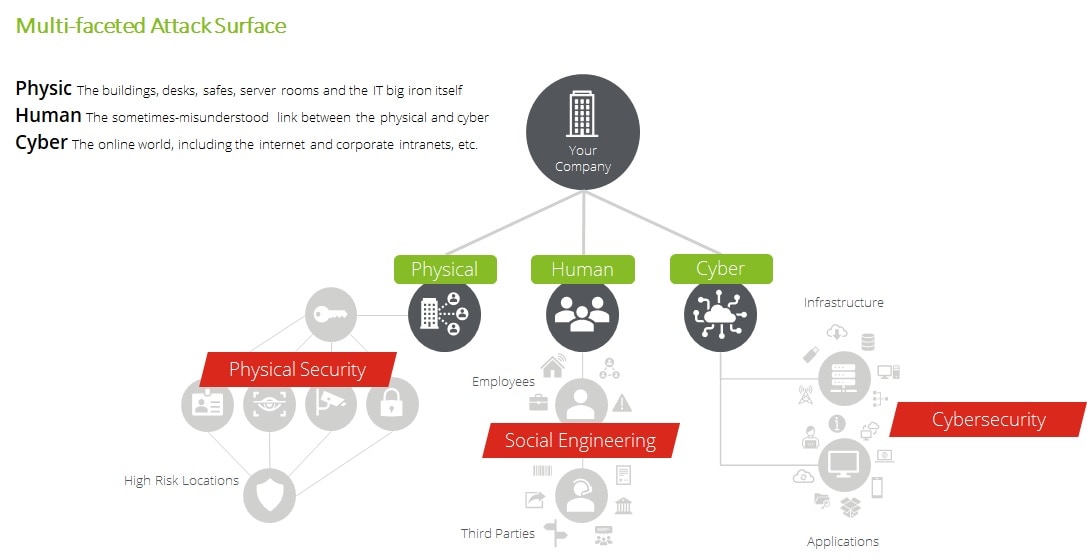
Current red teaming is designed to evaluate an organization's resilience against a wide range of attack vectors by looking at the organization's security posture from three main scope: Physical, Human and Cyber aspects. Unlike traditional cyber security practices that are defensive mode, Red Teaming is proactively simulate the real hacker's attack. They use threat intelligence, scenario-based simulations, social engineering techniques, and physical security testing to examining the organization's security posture.
The Role of Red Teaming Today
In today's digital world where the cybercrimes are rampant, red teaming becomes as a crucial component of comprehensive security strategies. In recent years more regulators globally require or/ strongly recommend organizations to take Red Teaming approach to validate the effectiveness of security controls and enhance incident response capabilities.
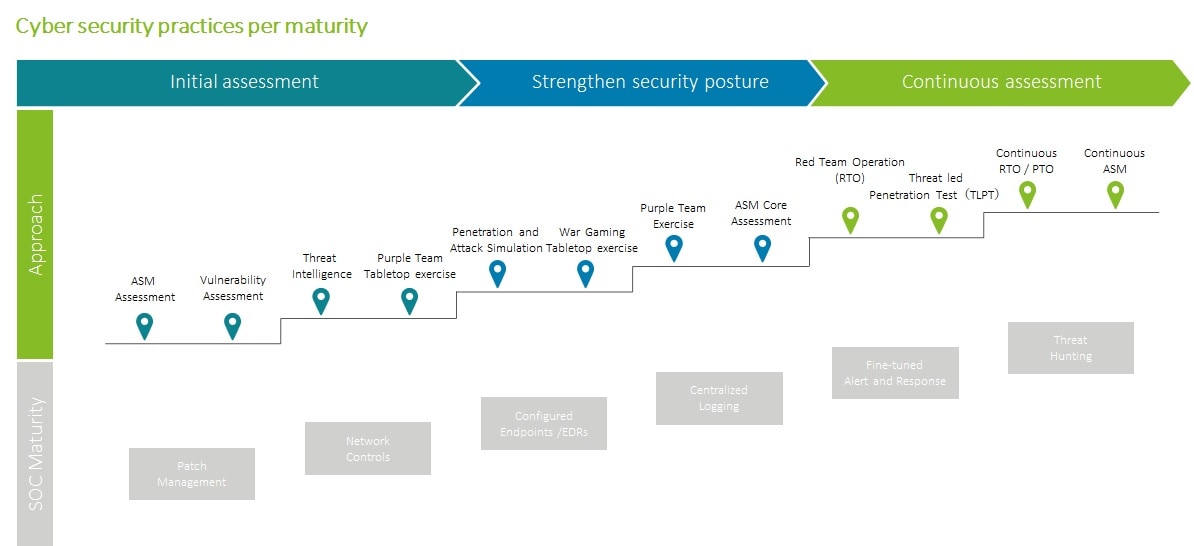
There are various level of red teaming exercises and organizations can take red teaming approaches which fit to their security material levels.
Moreover, some red teaming exercises such as war gaming is design to help executives to increase organization's incident resilience by validating the organization's incident response strategies and decision-making processes which goes beyond technical factors.
The Future of Red Teaming
As cyber security threats continue to evolve, the future of red teaming holds immense potential. Following are some key areas which are likely shaping the future of red teaming:
Automation: AI/Machine Learning enhanced tools like Breach and Attack simulation and automated penetration solution will be integrated into red teaming exercises, enabling automation of certain tasks, such as vulnerability scanning and attack simulations. At the moment the capabilities and scope of testing are limited but more the technology advanced, they will accelerate the efficiency and effectiveness of security assessment activities, enabling organizations to identify and mitigate threats more rapidly.
Physical Security: In Japan, organizations that conduct Red Teaming Operation tend to focus on social engineering and cyber aspect and less in physical security testing. Many incident cases shows that threats in physical aspect are critical equivalent to other two since organizations' physical environment are digitized and connected to cyber
Continuous Threat Assessment: Red Teaming become consecutive validations of organizations' security postures rather than a one-time evaluation. This way the red team can simulate the actual hacker's behaviors which often persistent to examining the targeted organizations and conduct attacks and allow organization to adapting to the dynamic threat landscape.
Conclusion
Red teaming become powerful means for organizations by embracing new technologies and adapting ever-changing threat landscape. Simulating realistic attack help organizations to identify their vulnerabilities and respond effectively.
Contact us
If you seek offensive security approach that adapt to your current security posture, let's discuss.
