Article

Cyber Compliance & Breaches
The current cybersecurity landscape is evolving rapidly, influenced by new legal regulations such as the Digital Operational Resilience Act (DORA), NIS II Directive, and enhanced data protection laws. These regulations aim to bolster the resilience of digital infrastructures, mandate stricter security measures, and ensure more robust protection of personal data.
As cyber threats become more sophisticated and pervasive, compliance with these frameworks is essential for mitigating risks and safeguarding critical systems. Organizations must adapt quickly, enhancing their cybersecurity practices to meet regulatory requirements and protect against escalating cyber threats. But you are not alone.
1. STEPS TOWARDS COMPLIANCE
Companies should foster close collaboration between their legal and compliance departments and IT and cybersecurity teams to ensure thorough compliance with applicable regulations. Regular training sessions and updates on emerging cyber threats and evolving legal requirements are crucial for maintaining effective compliance strategies. Additionally, conducting frequent audits, risk assessments, and incident response simulations will help identify vulnerabilities and strengthen the company's overall cyber resilience.
Early planning and preparation help organizations embed robust cybersecurity measures into their business processes. This proactive approach reduces costs and ensures necessary safeguards are in place to protect against emerging cyber threats, enabling secure and resilient innovation.
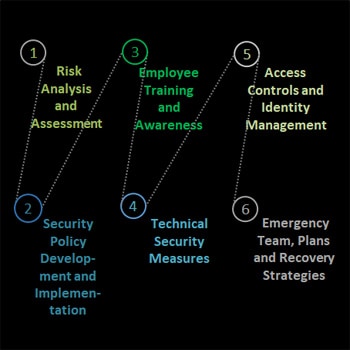
1. Risk Analysis and Assessment
- Conduct regular risk analyses to identify potential vulnerabilities.
- Evaluate the potential impact of cyber threats on the company.
2. Security Policy Development and Implementation
- Develop and implement comprehensive IT security policies.
- Regularly update these policies to address emerging threats and legal requirements.
3. Employee Training and Awareness
- Provide regular training to raise awareness of cyber threats and safe IT practices.
- Conduct phishing simulations and other tests to assess employee vigilance.
4. Technical Security Measures
- Utilize advanced security software and systems (antivirus, firewall, intrusion detection) in compliance with legal requirements and best practices.
5. Access Controls and Identity Management
- Enforce strict access controls to ensure that only authorized personnel have access to critical systems and data, in accordance with legal and regulatory standards.
6. Emergency Team, Plans and Recovery Strategies
- Develop a comprehensive incident response plan detailing actions during a cyber attack.
- Establish an emergency response team trained to handle cyber incidents.
2. LEGAL EMERGENCY RESPONSE
When dealing with a cyber incident, it is crucial to consider legal aspects such as regulatory compliance, data breach notification requirements, and potential liabilities. Legal guidance is essential to navigate complex laws and regulations, ensure timely and accurate reporting to authorities, and manage interactions with affected stakeholders. Additionally, legal counsel helps mitigate risks associated with potential litigation and contractual obligations. Having experienced legal advisors on hand is vital to effectively manage and resolve the incident while minimizing legal and financial repercussions.
RESPOND
- Identification / Initial Documentation: Quickly identify the scope and nature of the cyber incident and document all relevant details for later analysis and compliance.
- Damage Control: Implement immediate measures to contain the incident, limit further damage, and mitigate the impact on operations and data.
- Evidence Preservation: Secure and preserve all evidence related to the cyber incident to support investigations, legal actions, and compliance with regulatory requirements.
- Notification Obligations / Affected Parties’ Rights: Fulfill legal obligations to notify relevant authorities and affected individuals.
- Replacement Procurement: Arrange for the replacement of compromised systems or data, ensuring minimal disruption to business operations.
- Communication: Manage internal and external communications effectively, especially with supervisory authorities.
RECOVER
- Incident Recovery: Restoring systems and data after a cybersecurity incident.
- Contract Review: Evaluating agreements to ensure security obligations and responsibilities are met.
- Compliance Restoration: Ensuring that systems and practices adhere to regulatory and policy standards post-incident.
- Detailed Gap Analysis: Analyzing, what lead to the incident to strengthen and optimize resilience.
- (Further) Damage Control: Additional measures to mitigate and contain damage from a cybersecurity breach.
THRIVE
- Incident Recovery: Restoring systems and data after a cybersecurity incident.
- Contract Review: Evaluating agreements to ensure security obligations and responsibilities are met.
- Compliance Restoration: Ensuring that systems and practices adhere to regulatory and policy standards.
- Enhancing Resilience: Mitigate all gaps discovered in the gap analysis and implement further measures to enhance future resilience of the company.
At Deloitte Legal, we provide comprehensive legal advice to help clients prepare for cyber threats. Beyond ensuring compliance with regulatory requirements, we offer customized guidance in case of a cyber incident. Our approach integrates legal expertise with strategic insights to safeguard your interests and support your objectives.
Published: October 2024

Recommendations
Use of cloud services in the healthcare sector
Section 393 SGB V sets new requirements
Generative AI: A guide for corporate legal departments
What does the future hold for Generative AI and legal services?