Ransomware Readiness: The ransomware attack lifecycle Bookmark has been added
Human-operated ransomware attacks are very complex and devastating attacks on large enterprise networks. To adequately protect against, defend against and respond to ransomware attacks, it is very important to understand the life cycle of a typical ransomware attack.
The tactics, techniques, and procedures of ransomware threat actors can be quite different, but in many cases the attack life cycle will the same, as threat actors usually have two main objectives – to exfiltrate sensitive data out of the target network and to deploy a piece of ransomware to the enterprise-wide network.
This article will discuss and outline the various stages of human-operated ransomware attacks.
Initial attack vectors
Every ransomware attack starts from an initial access vector. Initial access to a network can be achieved using several techniques, including accessing a network via an unsecured or misconfigured VPN server or delivering trojan horse malware via a spear phishing attack. It is also possible to exploit public facing applications to deploy web-based command and control shells.
Statistics from recent attacks show that the three most common initial attack vectors used in ransomware attacks are Remote Desktop Protocol (RDP) compromise, spear phishing attacks, and the exploitation of software vulnerabilities.
RDP compromise
Remote Desktop Protocol (RDP) has consistently remained one of the most common vectors for threat actors to gain initial access a target network. The RDP protocol has been widely documented as the preferred initial access vector for SamSam and REvil ransomware operators.
The pandemic has accelerated and compounded this problem, as many organizations have had to provide employees with the capability to work remotely. In return, more servers have been exposed to the internet and have become attractive targets for various threat actors, including ransomware operators.
For example, we can utilize Shodan to search for publicly exposed servers with port 3389 open, which is the default port for Remote Desktop Protocol (RDP).
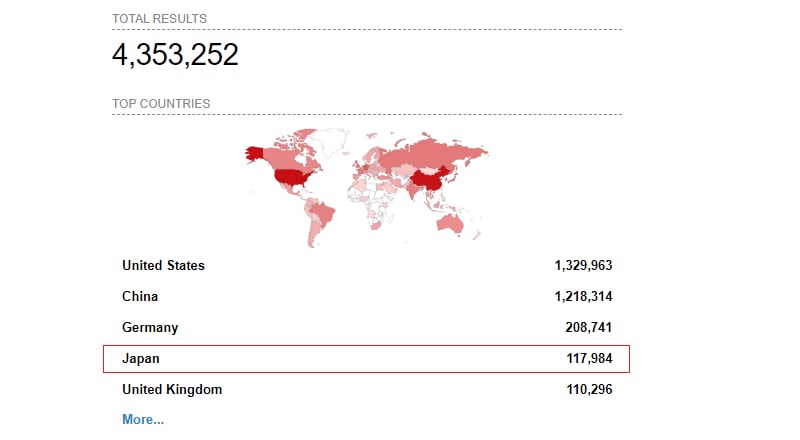
Figure 1 – Devices with port 3389. Remote Desktop (RDP) protocol exposed to the internet (Source: Shodan.io - Shodan Search Engine).
This query returns millions of results. Almost 118,000 in Japan alone. This is one of the reasons why this initial attack vector is very attractive and popular to ransomware operators.
In recent cases, ransomware operators will not attack the remote desktop servers themselves. They can simply buy remote access to corporate networks from other threat actors, dark web sources and underground forums.
Sources selling initial access to corporate networks are commonly referred to as “initial access brokers”. These brokers do not focus on post-exploitation activities, such as data exfiltration. Instead, they sell initial access to corporate networks or give it to ransomware operators for a percentage of the potential ransomware payment.
Spear phishing
Spear phishing is a social engineering technique aimed at tricking and convincing targeted users into opening malicious email attachments or clicking on malicious links. This technique is used by threat actors to infect and target host or endpoint with trojan horse malware.
Some common examples of ransomware trojan malware strains are BazarLoader, Hancitor, IcedID, Qakbot and Trickbot.
Spear phishing techniques can also be used to harvest account credentials. Threat actors will then use the harvested credentials to attempt to gain access to the target network via a public facing VPN server. Access is often achieved due to password reuse.
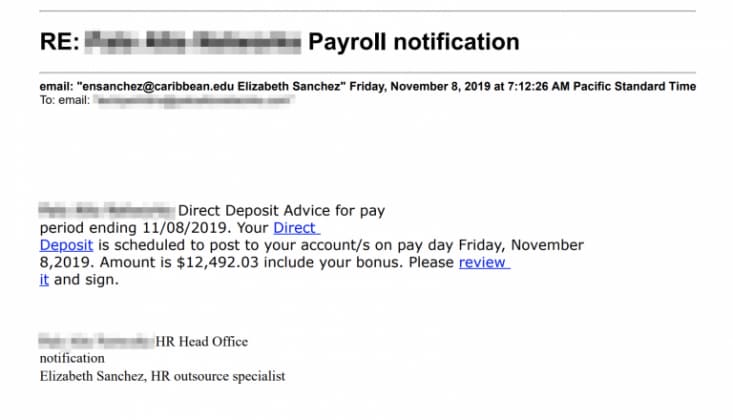
Figure 2 – A spear phishing attack example leveraged by Trickbot operators (Source: Deloitte Tohmatsu Cyber Malware Analysis and Research)
Software vulnerabilities
It’s important to note that not every software vulnerability can be used by a threat actor to gain initial access to a network. The most common types of vulnerabilities that allow access to a network are those that enable remote code execution or expose files to the internet that contain credentials.
Examples of this are CVE-2018-13379[1], a vulnerability in FortiGate VPN servers and CVE-2019-11510[2], a vulnerability in Pulse Secure VPN appliances. Both vulnerabilities were leveraged by ransomware operators to obtain access to plaintext username and password credentials. The credentials were then used to gain access to corporate networks.
CVE-2019-19781[3] is a remote code execution vulnerability in Citrix ADC and Gateway appliances. This vulnerability has commonly been used by ransomware operators to download and execute malicious code remotely and to perform post-exploitation activities.
In other case, highly sophisticated threat actors use even zero-day vulnerabilities, that is, vulnerabilities in systems or devices that have been disclosed but are not currently patched by the software vendor.
In July 2021, the REvil ransomware group successfully exploited multiple vulnerabilities in Kaseya's VSA remote management service and pushed a malicious update package that deployed ransomware. This attack impacted Kaseya’s customers including managed service providers. After realizing the large impact this attack had, REvil demanded over $70 million USD in ransomware payments.
Post-exploitation Techniques
Gaining initial access to a network is not the end goal of a ransomware attack. Once initial access has been achieved, threat actors will perform various activities to further enumerate a network, disable security controls, escalate their privileges, move laterally throughout the network, exfiltrate data and deploy a ransomware strain to achieve their objectives. There are a multitude of vulnerabilities, tools and techniques that threat actors use to achieve their objectives.
A very common vulnerability that is commonly exploited by several ransomware operators is CVE-2020-1472[4] or ‘ZeroLogon”. This vulnerability allows threat actors to obtain access to an Active Directory domain controller with a few very simply clicks of the mouse.
Threat actors will use common built-in Windows tools such as net.exe and nltest to perform network an Active Directory reconnaissance and enumeration. This technique allows threat actors to “Live off the land” and fly under the radar of security prevention and detection controls.
To expand and further the attacks, threat actors will download third party tools, most of which can be easily downloaded on the initially compromised host. Common examples of third parting tooling are PowerView, Bloodhound (Sharphound) and ADRecon.
These tools allow threat actors to enumerate and collect information about users and groups, computers, subnets, domain trusts, and to identify the relationships between objects in Active Directory.
Threat actors will also usually use a wide variety of tools, from network scanners to password and credential dumping tools. Common examples of these tools are, Advanced IP Scanner, Mimikatz, LaZagne, Process Hacker and ProcDump.
In some cases, using downloaded tools, threat actors may gain access to elevated credentials almost immediately. For example, mimikatz can be used to dump the Windows Local the Security Authority Subsystem Service (LSASS) process. This process memory contains cached credentials in memory. After dumping the process, attackers can gain access to these credentials.
Another very common and typical characteristic of human-operated ransomware attacks is the utilization usage of various post-exploitation and command and control (C2) frameworks. One of the most common post-exploitation frameworks is Cobalt Strike. This framework is leveraged not only by cybercriminals, but also by state-sponsored threat actors.
Cobalt Strike is only one example. Other common post-exploitation frameworks used in ransomware attacks include Metasploit, PowerShell Empire, CrackMapExec, Koadic And PoshC2.
These tools, most of which are open source and available openly on the internet allow ransomware operators to achieve multiple objectives such as scanning the network,elevate privileges, dumping credentials, download and execute third-party tools and scripts, lateral movement throughout a network and many more.
An additional important step for threat actors is to maintain long term persistent access to a network. This persistent access is achieved using several techniques. For example, a threat actor may hide a trojan in the Windows registry, add scheduled tasks to run payloads or simply install legitimate remote access software such as TeamViewer on system that have internet access.
Once the attacker has successfully performed reconnaissance and enumeration tasks and managed to elevate their privileges, this will proceed with their objectives - exfiltrating data and deploying ransomware across the network.
Data exfiltration
Data exfiltration often referred to as data exportation or data theft, is very popular with ransomware operators. Most ransomware threat actors main a Dedicated Leak Site (DLS). A DLS website is used to publish information about successful ransomware attacks and occasionally exfiltrated data if a company refuses to pay a ransomware payment.
Exfiltrated data frequently includes credit card information, Social Security numbers (SSNs), Personal Identifiable Information (PII), Protected Health Information (PHI) company private information and proprietary information and trade secrets. DLS websites are typically found on the dark web and can be accessed using the TOR browser.
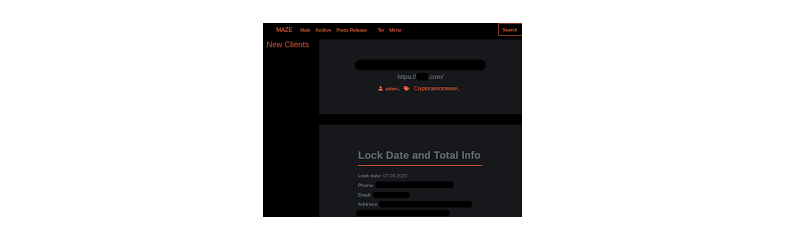
Figure 3 – Maze ransomware Dedicated Leak Site (DLS) (Source: Deloitte Tohmatsu Cyber Malware Analysis and Research)
Threat actors can spend a lot of time exfiltrating data from the compromised Network. This process may continue for months, maybe years if undetected.
During the attack life cycle, they may gain access to additional sensitive data and establish multiple scattered points of initial access throughout the network.
Threat actors can have dedicated servers for performing data exfiltration or they may exfiltrate data using the same post-exploitation command and control (C2) servers that are used during the attack life cycle.
Attackers commonly use coming legitimate tools for data exfiltration. For example, tools such as WinSCP or FileZilla. These tools may be extremely hard to detect particularly if an organization does not have a dedicated security operations center and monitoring team.
Some ransomware operators use public cloud storage, such as MEGA, DropMeFiles, and others to exfiltrate data. To exfiltrate data this way, the threat actors may use a regular web browser or, corresponding cloud storage client applications.
When sensitive data has been exfiltrated, the victim network is ready to be prepared for ransomware deployment.
Ransomware deployment
The Windows operating system has a built-in backup toolset called the Volume Shadow Copy Service. This toolset can create backup copies of files and volumes so that they can be restored to their previous state if required. Ransomware operators are very much aware of this feature. Most ransomware strains will disable this service and remove the backup copies.
Many ransomware strains have built-in functionality for wiping files with the extensions from backup solutions. For example, files with the following extensions will be wiped by TinyCryptor ransomware strain.
- .vbm
- .vib
- .vbk
- .bkf
- .vlb
- .vlm
- .iso
If security controls and solutions are operating properly, they may easily block this ransomware activity. However, at this point, ransomware operators have elevated privileges on the network and use the privileges to add ransomware strains to monitoring exclusions lists and disable security software and controls.
The attackers may also have Windows domain administrator credentials. Domain administrator credentials may be used to deploy batch scripts that disable security controls and deploy ransomware using Group Policy. In addition to Group Policy modification, common Windows administration tools such as the Sysinternal PsExec tool are used to deploy ransomware. The PSExec tool has the ability to execute processes on remote systems. If these techniques fail, ransomware can also be deployed manually.
Ransomware strains will not encrypt key Windows systems files during the deployment. Systems folders are in an exclusion list. This is to ensure that the system is available so that the victim can receive and email or portal link to establish communication with the ransomware operator.
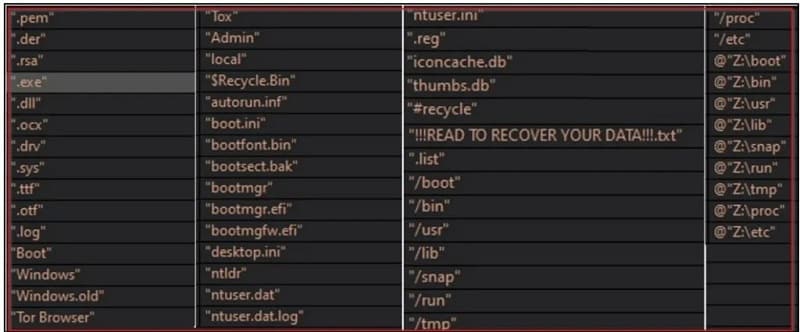
Figure 4 – Moisha ransomware file exclusion list. These files and folders will not be encrypted by the ransomware strain. (Source: Deloitte Tohmatsu Cyber Malware Analysis and Research)
Interestingly, the Tor browser folder is excluded from encryption. This is done to ensure that the victim can establish communication and access the ransomware operator’s portal on the dark web which is only accessible via the Tor browser.
When ransomware has been successfully deployed, the operators are ready to negotiate with the victim regarding the ransom amount. In a very small percentage of cases the ransomware attack may continue if the victim refuses to pay the requested ransom. For example, the Revil ransomware operators are known to perform Distributed Denial of Service (DDOS) attacks against victims who refuse to pay the ransom.
[1] Fortinet 社製 FortiOS の SSL VPN 機能の脆弱性 (CVE-2018-13379) の影響を受けるホストに関する情報の公開について (jpcert.or.jp)
[2] 複数の SSL VPN 製品の脆弱性に関する注意喚起 (jpcert.or.jp)
[3] 複数の Citrix 製品の脆弱性 (CVE-2019-19781) に関する注意喚起 (jpcert.or.jp)
[4] Netlogon の特権の昇格の脆弱性 (CVE-2020-1472) への早急な対応を (jpcert.or.jp)
