Core renaissance has been saved

Core renaissance Revitalizing the heart of IT
30 January 2015
As focus shifts from performing business processes to enabling innovation, reinvented core systems can form the foundation for growth and new service development.
Organizations have significant investments in their core systems, both built and bought. Beyond running the heart of the business, these assets can form the foundation for growth and new service development—building upon standardized data and automated business processes. To this end, many organizations are modernizing systems to pay down technical debt, replatforming solutions to remove barriers to scale and performance, and extending their legacy infrastructures to fuel innovative new services and offerings.
Investing in technologies that support the heart of the business has been IT’s emphasis since its earliest days—policy administration, claims management, and billing in insurance; order management, resource planning, and manufacturing for consumer and industrial products; inventory management, pricing, and distribution for retail; and universal needs such as finance and human resources. Core systems drive process and data automation, standardization, and intelligence—and represent decades of investment in buying packages, building custom solutions, and integrating an increasingly hybrid environment.
Learn more
View all 2015 technology trends
Create and download a custom PDF of the Business Trends 2015 report.
It’s not surprising that on average, 80 percent of time, energy, and budgets are consumed by the care and feeding of the existing IT stack.1 Within the core, unwanted technical debt2 and complexity likely exist, with systems at various stages of health, maturity, and architectural sophistication. But the core can also be a strategic foundation that enables experimentation and growth. Leading organizations are building a roadmap for a renaissance of their core—focused not on painting their legacy as the “dark ages,” but on revitalizing the heart of their IT and business footprint.
Business first
Amid continuously evolving business pressures and technology trends, several questions arise: How will the core hold up? (Consider, first, the business angle.) How well do existing solutions meet today’s needs? (Consider not just functional completeness, but increasingly relevant dimensions like usability, analytics insights, and flexibility to respond to changing business dynamics.) Does the core IT stack help or hinder the achievement of day-to-day goals across users, departments, processes, and workloads?
Of course, underlying technical concerns are also important. But their impact should be quantified in business terms. Translate the abstract specter of technical debt into business risks. Technical scalability can be measured in terms of limitations on growth—thresholds on the number of customers, orders, or payments that can be transacted. Reliability concerns translate into lost revenue or penalties for missing service level agreements due to outages or service disruptions. A lack of integration or data management discipline can not only delay the backlog of projects aimed at improving existing services, but also result in opportunity costs by constraining efforts to build upon the core for new mobile, analytics, social, or cloud initiatives.
Most IT leaders understand the looming importance of addressing issues in the core. In a Forrester survey of software decision makers, 74 percent listed updating/modernizing key legacy applications as critical or high priority.3 But the challenge is shifting from acknowledging a potential issue to making an actionable recommendation with a supporting business case and roadmap.
More broadly, consider the organization’s evolving business strategy, be it organic growth, new product innovation, mergers and acquisitions, or efficiency plays. What role does the core play in seeing that strategy unfold? Also consider how to revitalize and extend current investments by using existing assets as foundational elements in the future.
One size does not fit all
Core renaissance efforts are born from this combined view of business imperatives and technical realities—balancing business priorities and opportunities with implementation complexity. Approaches will vary from wholesale transformational efforts to incremental improvements tacked on to traditional budgets and projects. But regardless of how systematic or tactical they are, core renaissance responses typically include a combination of the following five approaches:
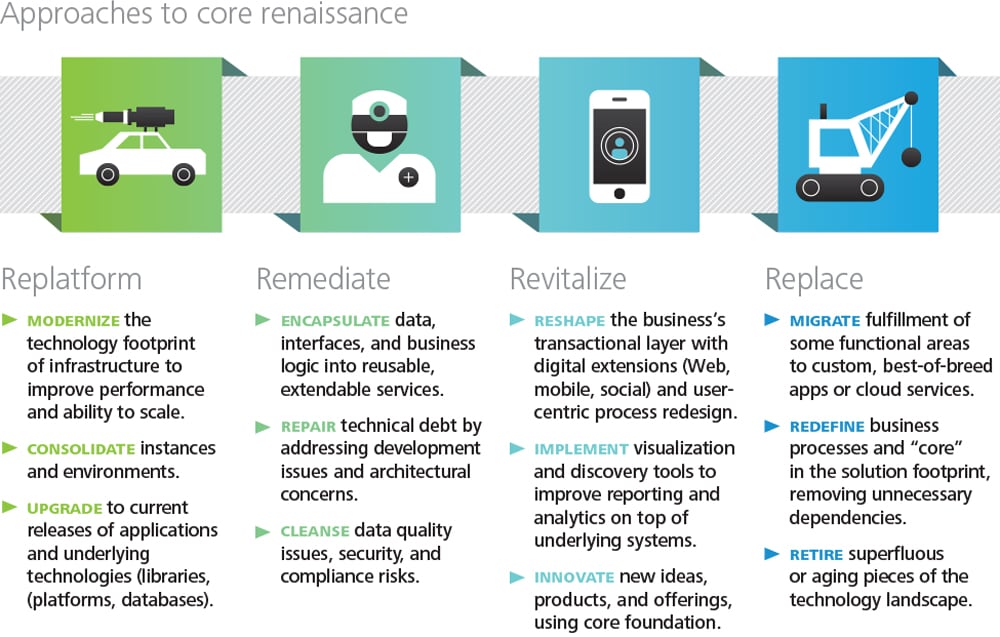
- Replatform: Replatforming efforts typically center on upgrading the core application or implementing new solutions on the underlying platform upon which the application runs. For ERP, replatforming could involve technical upgrades, migration to latest software releases, or instance consolidation. For any software solution, it might also include moving to modern operating environments (server, storage, or network), adoption of in-memory databases, or shifting to cloud infrastructure or platform services. While it may appear less invasive than other approaches, replatforming is rarely a simple “lift and shift” exercise. It typically requires a workload-by-workload analysis and surgical intervention to prepare for and achieve the shift.
- Remediate: Similar to replatforming, remediation shifts attention to the internal workings of systems. For custom solutions, this could involve rewriting chunks of code to reverse technical debt. For ERP, it might include unwinding customizations for capabilities now handled by out-of- the-box software, or updating modules to better manage master data by pointing to a common system of record instead of having everyone maintain a separate version of customer, product, or supplier data. For all software, it might involve rewriting or wrapping interfaces to promote reuse, making the necessary logical and architectural changes to allow core data and transactions to be exposed via mobile, social, or cloud apps.
- Revitalize: In some cases, the internal business logic and transactional capabilities are rock solid, but the usability of the systems causes pain points—for instance, because of poor user experience design, long response times, or a lack of mobile versions to support business when and where it actually occurs. Both analytical and transactional solutions can benefit from revitalization. Approaches start with a user-centric, persona-based focus—understanding customer, employee, and partner needs by observing them in the field. Existing processes, reports, or screens shouldn’t constrain new solutions. Instead, they should be built around how individuals actually should and could do their job, empowered by technology. Well-designed front-end solutions allow existing back-end services to be hooked into them without much effort; in many cases, however, some degree of remediation will be required to support revitalization goals.
- Replace: Sometimes, the right answer is to recast the solution landscape by replacing parts of the portfolio with new solutions. In industries like insurance and public sector, large-scale custom solutions were often necessary decades ago because of a lack of commercially viable packaged solutions. New entrants and offerings have closed many of these gaps, giving institutions a chance to revisit “build” versus “buy” decisions. Similarly, cloud offerings can be attractive to companies looking for improved agility and the potential to reallocate capital expenditure to operating costs. Importantly, IT needs to be a part of these discussions; otherwise, lines of business may make their own isolated investments.
- Retrench: Retrenchment, simply put, means doing nothing. This is likely a part of any core renaissance journey, especially for non-differentiating parts of the business and IT footprint. Being passive can be strategic, especially if not taking action is a deliberate decision made after careful analysis. This is not the same as ignoring an issue; it is weighing the risks, communicating the recommendation (and potential repercussions) to key stakeholders, and then deciding to focus on other priorities.
Beyond technology
For any of the techniques described above, the technology implications are only part of the renaissance of the core. Business processes need to evolve in line with modernized solution stacks, potentially requiring new talent with new skills as well as the development of existing staff. Likewise, IT organization structures and delivery models may need to change to put in place mechanisms to support new technologies and maintain commitments to modernized solutions. Every new system or bit of code can either be on-strategy or create the next generation of technical debt. IT should invoke a mantra of institutionally “doing no harm” while also raising its game to help drive innovation and growth. Adoption of DevOps,4 agile, and industrialized approaches to fostering innovation can help. But just as essential is the alignment to broader business objectives—for even nuts-and-bolts technology investments to have some grounding in business priorities and outcomes. CIOs operating as chief integration officers5 should have that grounding. They can use core renaissance as a platform to manage the IT portfolio with eyes wide open, revitalizing and extending their existing assets to not just better meet the needs of today, but lay the groundwork for tomorrow’s breakthrough ideas.
Lessons from the front lines
Delivering the future
Sysco, a leading food marketing and distribution company, delivers more than a billion cases of food, equipment, and supplies each year to restaurants, hospitals, schools, and other customers. Like many businesses today, Sysco aims to execute its mission of providing fast, consistent, and reliable deliveries while simultaneously pursuing new growth opportunities made possible by emerging technologies.
“Building upon the company’s existing IT foundation in ways that support growth while maintaining critical services requires planning and balance,” says Wayne Shurts, Sysco’s chief technology officer. Shurts describes Sysco’s approach to core revitalization as resembling a triangle, with core systems forming the base. Sysco has dozens of systems that support everything from warehouse operations and delivery truck logistics to ERP and CRM. The company’s IT organization focuses on maintaining the reliability of core operations by minimizing the technical debt within these core systems through regular upgrades and routine “care and feeding.” Reliability and performance are IT’s mantra, given Sysco’s mission-critical, high-velocity operations. Moreover, these core systems yield a plethora of transactional data that can fuel new, strategic initiatives.
The second side of the triangle provides agility—the ability to react quickly to business and customer needs. Using a variety of cloud-based services, Sysco applies iterative development techniques to rapidly develop and deliver mobile and social apps to warehouses or restaurant floors. These apps are created specifically to add value where the work gets done. Because of this, speed is important: IT needs to test concepts quickly, discard those that don’t pan out, and rapidly scale those that do.
The third side of Shurts’s triangle provides analytics that help generate the insights needed to improve operations—spanning the company’s warehouses to its customers’ kitchens. By combining and analyzing data sourced from its own systems as well as from partners, customers, and third parties, Sysco is able to generate new insights across customers and markets, sales and marketing, and business operations. For example, the company helps restaurant owners better organize their menus, manage inventories, and run their operations. A company’s ability to deliver value-added services increases when its core systems are modernized and revitalized.
To help Sysco employees keep their skills current amid technological and operational changes, the company has developed a formal program that maps out competencies for current and future positions and helps workers create personalized development plans. It also provides training to help them better execute their current jobs and to prepare for future roles. Finally, the company emphasizes college recruiting to introduce new talent with different approaches into the workforce.
Shurts’s triangle strategy for core revitalization is delivering results. For example, using the agility side of the triangle, IT has built solutions used by the shared services organization to improve credit and dispute processing across multiple operating entities. And analytics is helping Sysco improve transportation logistics by improving fuel use and the selection of routes its trucks travel.
Engraving, printing, and modernization
The Bureau of Engraving and Printing (BEP) is the largest producer of security documents in the United States, printing billions of Federal Reserve notes, portions of US passports, materials for the Department of Homeland Security, and naturalization certificates. The legacy technology at BEP resulted in operational inefficiency—a challenge made more difficult by non-unified systems that provided limited visibility into end-to-end operations. The bureau also used manual processes to reduce spoilage and improve accountability.
In 2009, BEP launched a multi-year, enterprise-wide transformation initiative, referred to as the BEP Enterprise Network (BEN) program, to retire and modernize its older mainframe technology. Leadership saw this project as an opportunity to team with IT to introduce the latest capabilities in diagnostics, intelligence, and automation across the manufacturing spectrum at BEP.
The BEN project team took a mixed approach to modernizing its core systems. Team members replaced the mainframe manufacturing and financial systems with a set of open, tightly integrated, and scalable commercial off-the-shelf business applications. They also enhanced printing presses with embedded intelligence and instrumentation capabilities. These enhancements provide a custom front-end application to the production floor employees that includes automated dashboards with alarms and notifications for printing press status. Additionally, the centralized data warehouse reduces the time required to collect data across production areas, and has brought historically unavailable data online. With better data coming from these applications, the team was also able to introduce predictive analytics and near real-time data analysis.
The BEN project has enabled stronger collaboration among working teams and streamlined operations in a number of ways. For example, BEP has retired 23 disparate legacy applications while introducing industry-standard business processes and tools. The time required to report monthly financial results has been significantly reduced. Automated data entry processes and preventative maintenance schedules have boosted the productivity and reliability of bureau resources. Finally, new security measures have improved the overall accountability and transparency of reports and production status.
Through what has been a truly transformative program, BEP has realized its goal of modernizing its systems while advancing the vision of becoming a more information-driven, 21st-century organization. Moreover, BEP plans to maintain its current momentum with BEN by introducing more features that can help uncover hidden data trends and produce graphically rich analyses.
Filling the gaps with best-of-breed
A leading semiconductor company realized recently that its core systems needed to be modernized in order to meet changing needs. The company’s business had evolved considerably over the past several years, but many of its systems and processes relied on ad-hoc operational environment and suboptimal solutions.
To create greater consistency and efficiency across systems and processes, leadership set a goal of achieving 15 percent more efficiency and 15 percent less overhead. The company approached this and other strategic goals by adopting technologies like cloud, analytics, and mobile; by streamlining reporting processes; and, importantly, by revitalizing infrastructure to create a platform for adopting future technologies that could drive further optimization over the next decade.
As the company began drawing up plans for meeting leadership’s targets, it identified four major areas that could, if upgraded with new technologies, potentially provide significant value: operations planning, supply chain, B2B customer service, and warehouse operations. Yet planners realized that a single enterprise solution likely would not meet all requirements in these and other critical areas. Project leaders decided that, rather than be tied to one vendor, they should deploy several best-of-breed cloud-based solutions from boutique vendors to fill ERP functionality gaps in CRM, distributions, and demand planning, among others.
To revitalize its existing infrastructure, the company could easily have spent tens of millions on servers, databases, and other infrastructure components. Instead, project leaders opted to create a private cloud and to virtualize much of the needed infrastructure capabilities, which cut the price tag roughly in half.
When the newly revitalized core and the other systems become fully operational later this year, the company expects they will provide the consistency, optimization, and efficiency it set out to achieve. Moreover, these components, working in tandem with an infrastructure that has been transformed by virtualization, can serve as a platform for future innovation efforts.
My take
Terry Milholland, chief technology officer,
Internal Revenue Service
2014 saw one of the smoothest filing seasons ever for the IRS. It’s an encouraging sign that our efforts to turn the agency’s IT department into a world-class organization are paying off. Beyond supporting the IRS’s customer-centric transformation, we wanted to evolve IT to deal with the complexity of our operations. Budgeting processes are complicated and unpredictable. Tax implications of legislation like the Affordable Care Act need to be codified for the hard deadlines of the tax season. Decades-old technologies require modernization. But our team has risen to the challenge, and we’re seeing tremendous results.
We’ve created a vision for IT to be on a par with Fortune 100 organizations, and that affects our people, process, and technology. At the center of the technical vision are data and services—allowing our core systems to interact with each other and keeping teams from repeating their efforts. We now have a logical and physical data model for the full submission process—more than 30,000 attributes manifested across our core. Coupled with a service-oriented architecture, we’re creating a repeatable approach to building on top of our core—to be able to add new technology in a transformational way, responsive to mission needs.
Which is where process comes in. We’re committed to an agile methodology—using our new standards to modernize and grow. We have selected a set of technology standards that the organization follows to increase productivity and quality; we’re already at level 3 for CMMI and ITIL.6 The impact on quality has been very real, and has helped break down barriers between the different teams and pieces of the technical stack.
But it comes down to our people. I don’t lead with a “thou shalt” attitude. Instead, we enlist leaders in the organization—the men and women who have influence in the work environment and can pave the path for others. We solicit their feedback on our direction, working with them to iron out the details, and being open about issues, ideas, and concerns. These “guild masters” can help convince their teams to believe in the vision, to do things differently, and to positively impact the culture. Openness has become part of our organization. On projects, anyone can raise an objective. We record it, then we disposition it. Their opinions are listened to and the “Oh, they never ask” attitude doesn’t exist.
Whether private or public sector, IT departments face constraints when it comes to taking on projects—let alone modernizing legacy systems and tackling their technical debt. If I look back on the past fiscal year, we started with a 16-day government shutdown that meant we had 90 percent of our workforce out and created uncertainty about our annual budget. But we continue to push forward with our strategy to transform our legacy systems. We’ve only just begun our journey toward modernization. We are going to keep adding new technologies in a transformational way—despite, and in some cases because of, people and fiscal constraints. Our focus on technology, process, and more importantly, people will get us there.
Cyber implications
Some organizations treat ownership and control as a proxy for managing risk. Because the “core” is often software built on-premises or bought, this approach suffers from a twofold misconception. The first is that the existing stack is reasonably secure. The second is that moving to new technologies, be they mobile, social, or cloud, inherently raises the risk profile. Neither is universally true, and both raise the need for strategic handling of cyber security concerns.
The notion that today’s IT footprints are secure enough is a dangerous one. Legacy projects may not have considered compliance, contractual, or risk-based requirements adequately, if at all. A lack of strategic focus and budget has relegated many security initiatives to compliance and control activities—adding scope or causing rework to address vulnerabilities discovered late in the development cycle. Reactionary measures are taken when high-profile breaches occur, typically targeting known threats linked to particular incidents. A more comprehensive approach to cyber security is needed, acknowledging that it could be exorbitantly costly to protect against every potential attack.
Organizations should identify the cyber “beacon” that is likely to attract threats. Resources should then be directed against assets that potential attackers may likely find most valuable, or those that, if compromised, could cause greatest damage. Beyond securing against attack, organizations should monitor emerging threats and potentially reallocate resources as their cyber beacons change—practicing vigilance, not just security. They should prepare for how to detect, contain, and respond to potential incidents. There may be no such thing as a hacker-proof organization, but you can still be resilient in the face of an attack. Hope and luck are not strategies; even if the core has not been compromised, that does not mean it is secure. Building out cyber security capabilities can help close the gap.
The misconception that emerging technologies are inherently riskier than legacy assets is common, as is the myth that on-premises solutions are always more secure than cloud alternatives. Privacy concerns typically dominate discussions around social—requiring policy, training, and monitoring to guide appropriate behaviors. Mobile concerns fall between security and privacy, especially as enterprises are embracing “bring your own device” and “bring your own app” strategies. The approach described above can help, with a mindset anchored in probable and acceptable risk. Prepare for strategies to secure information at the device, application, and, potentially, data level while being sensitive to the overall user experience. Security tops concerns about public cloud adoption, with the rationale that large infrastructure-as-a-service, platform-as-a-service, and software-as-a-service providers are obvious and lucrative targets for cyber criminals. But with the escalated potential bounty, public cloud vendors also typically have highly sophisticated security tools, procedures, and personnel that can be more effective than many company and agency in-house cyber defenses. Who is better prepared to win the cyber arms race? Cloud providers whose livelihood likely depends on their ability to prevent and respond to incidents? Or organizations that have historically had trouble justifying security and privacy budgets as a priority? Either way, the obligations of the organization as the acquirer and custodian of data do not go away. Leverage providers to help outsource risk if cyber isn’t a core strength, but recognize that your organization still retains responsibility for its security.
Again, there is no universal answer. Security and privacy should not be a blanket objection that curtails core renaissance, but they should be baked into the overall approach—setting the right foundation for a revitalized core and guiding new investments in areas that will form the core of tomorrow’s business.
Where do you start?
Sparking a renaissance of your core can be a daunting pursuit for value—potentially expansive in scope and ripe with risk—that will likely require effort to put in terms the business will understand. Fearless leaders might savor the opportunity for legacy-building. But for the rest, is the payoff worth the strife?
The fact is, CIOs don’t have a choice. As the stewards of the technical footprint, they are responsible for the core’s care and feeding. Whether expressly labeled as “modernization” efforts or responses to unplanned incidents and outages, or embodied in extra project cost and complexity due to unforeseen technical debt, the core will continue to demand attention. The question becomes how proactively it will be addressed—and whether it will be enough. Here are some specific areas in which to potentially undertake initiatives:
- So you’re saying there’s a plan. Core and legacy concerns are found wherever IT investments exist. They inspire a sense of universality and inevitability—the enterprise equivalent of “death and taxes.” But they are not irreversible—and they don’t have to be seen as an albatross. Aikido is a form of martial arts that uses the mass of the attacker to one’s advantage. Core renaissance can trade off of the magnitude of existing investments in similar ways, but it will not come across surreptitiously. It requires an informed, thoughtful position that balances business needs with the limitations of existing systems and the potential of emerging technology.
- Spark a light. Massive investments can be tough to stomach, especially if the “so what” seems limited to behind-the-scenes machinations. Find a lingering opportunity or burning platform—ideally, one that resonates with a part of your business that is likely to become an advocate for broader goals. A bottom-up approach to new organizational structures, processes, and skill sets is an effective plan of attack—assuming enough of a direction has been established so that experiments are pointing toward where you want to go.
- Plant the seed. In Deloitte Transition Labs with newly appointed CIOs, leaders report that 63 percent of their time is focused on the care and feeding of the technology footprint. The complexity embedded in the core perpetuates the cycle. These same leaders desire the inverse, believing they could better serve their companies by focusing 66 percent of their time on being a strategist or catalyst for growth and innovation.7 Deliberate investments in revitalizing the core can help close this gap. It may take time, but will likely lead to lasting effects.
- Don’t go it alone. Large enterprises have developed a healthy skepticism around emerging technologies. Vendor fatigue and aversion to “shiny object syndrome” are partially to blame. The age-old practice of circumventing IT to sell directly into the business is also still being felt, leading to “shadow” IT organizations and even more complexity in the core. But resistance to change is in many ways futile. Hunkering down will likely just reinforce the shadowy end run directly into the business. The cruel irony: New solutions will likely eventually find themselves back at IT’s doorstep, either for enterprise-level support or because business processes require integration with the core. Instead, pick a few strategic vendors to partner with to enable core renaissance. This may involve co-investment (for example, sharing risk or product roadmaps), proactively prototyping new ideas, providing briefings on industry (and cross-industry) leading practices, or brokering introductions to interesting new solutions for specific business scenarios.
- Verbs, not just nouns. Technical components are rightly critical parts of core revitalization, but pursuing core renaissance is also an opportunity to transform how you build and support solutions. Aim to embed design as a discipline8 into everything you do, working back from the user experience, not up from the systems and data. Look to embrace pieces of DevOps: automated environment provisioning, requirements management, continuous build/configuration management, testing automation, one-touch deployment, and systems maintenance and monitoring solutions. Finally, create a living approach to architecture—guiding not just the solutions and platforms that are blessed, but their usability, integration, data, and security considerations.

Bottom line
Disruptive forces are reshaping industries: globalization, emerging technologies, new customer engagement requirements, diminishing competitive barriers to entry, evolving regulatory and compliance requirements, and persistent threats around security and privacy. All of these are inextricably linked to technology, moving the core to center stage. Some modernization will no doubt be needed to keep the lights on as the business scales up. But beyond table stakes, a revitalized core could become a strategic differentiator. A renaissance of the core amid an elevation of IT to support the heart of the business can lay the foundation for the organization to experiment, innovate, and grow.
© 2021. See Terms of Use for more information.


