Attack Surface Management (ASM) is a proactive approach that plays a crucial role in defending against cyber threats by identifying organization's IT assets and minimizing their potential vulnerabilities. In this article, we'll delve into the practices for effective Attack Surface Management to help safeguard your digital assets.
In today's rapidly evolving digital landscape, cybersecurity has become an indispensable concern for businesses and organizations. As technology advances, so do the methods and techniques that threat actors use to breach systems and steal valuable information. Attack Surface Management (ASM) is a proactive approach that plays a crucial role in defending against cyber threats by identifying organization's IT assets and minimizing their potential vulnerabilities. In this article, we'll delve into the practices for effective Attack Surface Management to help safeguard your digital assets.
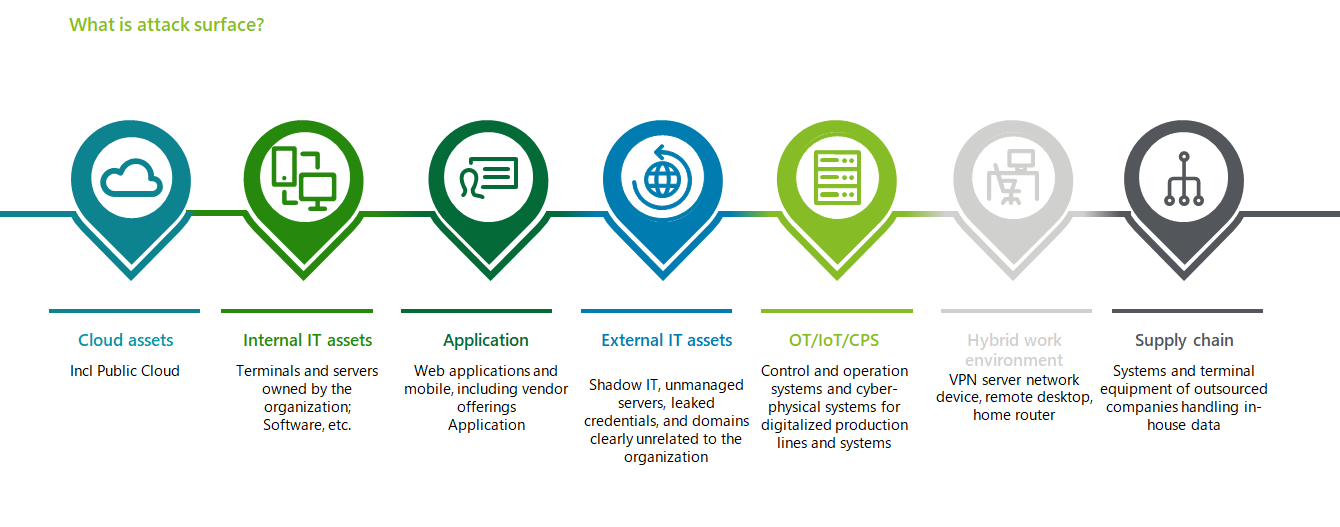
What's your Attack Surface?
For your cyber security teams to effectively manage an attack surface, they must first understand what it encompasses, and what they’re essentially responsible for defending and protecting.
An attack surface consists of the potential system, network or application infiltration or entry points and unprotected assets that can be targeted or exploited by malicious threat actors to breach and gain unauthorized access to an organization. The larger the attack surface, the more potential targets are available to a threat actor.
Traditionally, IT management`s view of ‘assets’ has focused solely on computer devices and servers. However, applications, people, and processes associated with traditional assets provide just as much value to the organization and generate just as much risk.
The modern, secure approach is that any asset that a threat actor can potentially leverage to infiltrate your organization should be considered a part of your attack surface. Therefore, any asset with a cyber context, from IoT devices, IP addresses, APIs to URLs and the users themselves are part of the organization`s attack surface.
Why is ASM important?
Managing a growing attack surface is an overwhelming concept for any organization, especially for those with thousands of employees, and hundreds and thousands of devices, applications, and assets. This increased risk has put more responsibility on security teams, who are being called upon to carefully manage the organizations attack surface. To effectively increase visibility and prioritize security workloads, attack surface management will address several organizational security challenges, such as the following:
- Reducing Vulnerabilities: By actively managing the attack surface, you can identify and mitigate vulnerabilities and weaknesses in the systems and applications. This proactive approach helps prevent potential exploits before they are discovered and abused by attackers.
- Enhancing Security Posture: Attack surface management allows you to gain a better understanding of your overall security posture. It helps you identify high-risk areas and prioritize security efforts to strengthen your defenses where they matter most.
- Minimizing Risk: A larger attack surface means more potential opportunities for attackers to breach your organization. By managing the attack surface effectively, an organization can minimize its risk exposure and improve its resilience against cyber threats.
- Early Detection and Response: A well-managed attack surface makes it easier to monitor and detect suspicious activities. Organizations can respond quickly to potential threats, limiting the damage caused by cyber incidents.
- Business Continuity: Effective attack surface management contributes to business continuity and resilience. By reducing the likelihood of successful cyberattacks, organizations can avoid costly downtime, reputation damage, and potential legal consequences.
- Cost-Effectiveness: Identifying and addressing security weaknesses early on is more cost-effective than dealing with the consequences of a full-scale cyber breach later.
How to manage your attack surface?
Following are some tips to start building your attack surface management strategy in order to proactively reduce your exposure to potential threats, safeguard your digital assets, and enhance your overall security posture. Remember that attack surface management is an ongoing process that requires continuous assessment, adaptation, and vigilance to stay ahead of emerging threats and vulnerabilities. Start your journey today, and build a strong defense against cyber threats.
Following are strategic tips for starters;
(i)Start with a complete attack surface analysis
If you aren’t aware a potential access point exists in the first place, you can’t possibly defend against today’s advanced cyber threats. Gathering a consolidated view and understanding of *everything* that lies within the attack surface is the first step in managing it.
To get started on your attack surface management journey, collect the following information.
- A multi-dimensional view of all assets, particularly internet facing assets.
- The current state for each asset and entity.
- Maps of relationships between all assets from a cyber security context.
(ii)Assessment and Management
Assessment involves understanding which assets and areas of your attack surface represent real risk and identifying vulnerabilities before the threat actors do. Management involves prioritizing and mitigating the risks, as well as monitoring for changes in the attack surface.
(iii) Use tools and services that can help you discover your attack surface.
Automated tooling and third-party consultancy services can quickly scan and crawl your organization`s attack surface to identify attack vectors, risks and vulnerabilities, as well as monitoring for changes in your attack surface. Example: DTCY ASM.
(iv) Don`t forget about third-party vendors
Your attack surface also includes your third-party vendors that process or store your data. Assess your third-party vendor`s security posture to ensure they are following best practices. Monitor for changes in their attack surface that could affect your organization.
(v)Leverage security automation and insights from cyber security experts.
Manual, time-intensive tasks are not only scalable—they’ve become impossible for security teams that are already struggling with limited resources. Automate wherever possible to take your attack surface management strategy to the next level. Understandably, you may want to start small with automated discovery and assessments, and eventually move on to automatic remediation of coverage gaps. DTCY automated solutions and cyber security experts can help you with this step.
プロフェッショナル

大場 正士/Tadashi Oba
サイバーセキュリティの領域において20年以上の経験を有し、主に金融機関を対象としたサイバーセキュリティの改善支援を手掛けている。 特にRed Team Operationsや脅威ベースのペネトレーションテスト(TLPT)等のサイバー攻撃者目線で行う侵入テストによるサイバーセキュリティ評価を多数提供。 >> オンラインフォームよりお問い合わせ