Offensive security practices are important for understanding and mitigating ransomware attacks because they involve proactive measures aimed at identifying vulnerabilities and weaknesses in businesses' IT infrastructure. The more ransomware attack become frequent and sophisticated, prompting the urgent need for offensive security practices. This article explores the growing ransomware threat landscape and emphasizes the crucial role offensive security plays in mitigating these risks.
Evolving Hacker Tactics Pose New Threats
According to Deloitte Threat report, Approximately 71% of organizations worldwide were affected by ransomware in 2022, a trend likely to continue for 2023. These malicious cyberattacks, typically perpetrated by highly skilled hackers, encrypt valuable data and demand a ransom in exchange for its release. The ransomware landscape is constantly evolving, with hackers employing new tactics to maximize their impact and financial gain.
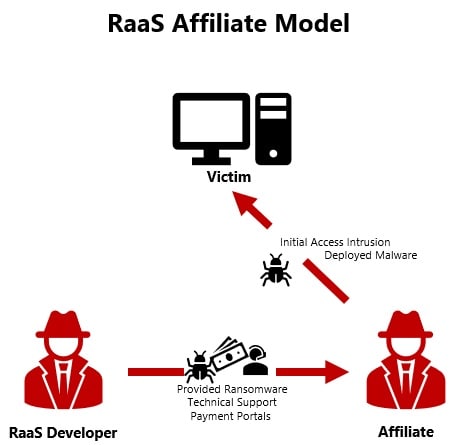
Ransomware as a Service (RaaS): One notable trend is the emergence of Ransomware as a Service (RaaS). This model allows even less technically proficient hackers to launch attacks by providing them with ready-to-use ransomware tools. Ransomware accounted for approximately 20% of all cyber breaches in 2022 with the ease of use of RaaS kits. RaaS platforms offer user-friendly interfaces, customer support, and profit-sharing schemes, enabling a wider range of individuals to partake in cybercrime. This shift has led to an exponential increase in the number of ransomware attacks.
Double Extortion Techniques: To further enhance their financial gains, hackers have adopted a strategy known as double extortion. Traditionally, ransomware involved encrypting data and demanding a ransom for its release. However, in recent times, hackers have expanded their approach by stealing sensitive information before encrypting it. They threaten to expose or sell the stolen data unless an additional ransom is paid, adding another layer of urgency and incentivizing victims to comply with their demands.
Supply Chain Attacks: Hackers have recognized the value of targeting supply chains as a means of infiltrating high-profile targets. By compromising a trusted supplier or vendor, they can gain access to multiple interconnected systems and networks. The case of a cyber attack on The regional medical center in 2022 was an example of the cyber attacks caused from vulnerable spot of supplychain. After cyberattackers illegally infiltrated the data center of a catering company, they spread the intrusion to the hospital which was connected to a closed VPN network.
Exploiting Zero-Day Vulnerabilities: Zero-day vulnerabilities, which are software flaws unknown to developers, are highly sought after by hackers. These vulnerabilities provide an opportunity to exploit systems without immediate detection or remediation. Ransomware operators actively search for and acquire zero-day vulnerabilities on the dark web, using them as entry points for their attacks.
Targeting healthcare and hospital industry: According to Trendmicro, the number of ransomware detections worldwide for the medical industry become in the top three with public, banking in 2021, while banking, public, and manufacturing are the most common in 2020. Hackers are acutely aware of the significant leverage they possess when targeting critical industries, making it an attractive and lucrative avenue for ransomware campaigns.
Beyond expanding methods to secure payment, Deloitte assesses with medium-high that ransom demands are also likely to increase in 2023. This increase in ransom demands would follow a steady climb since 2021 when ransoms saw a 518% increase over 2020. Oversea mail service provider was extorted by LockBit for $80 million in February 2023, the largest ransom demand since a $50 million demand in 2022.
The Urgent Need for Offensive Security Practices
Here are a few offensive security practices that are crucial in the context of ransomware attacks:
Vulnerability discovery: Offensive security practices, such as penetration testing or ethical hacking, can help identify vulnerabilities and weaknesses in an organization's systems and networks. By actively trying to exploit these vulnerabilities, organizations can gain insight into potential entry points for ransomware attacks. Furthermore, we see that advanced businesses are adapting Attack Surface Management which is another approach to understanding how the organization's IT assets look from the attacker's point of view. These proactive practices allow businesses to patch or mitigate these vulnerabilities before attackers discover and exploit them.
Attack simulation: Offensive security practices simulate real-world attack scenarios, including simulations designed for ransomware attacks. Ever evolving technology like BAS and automated pen-testing tools helps organizations to conduct testing yet, a strategic roll-out plan and highly technical analysis are required to get the full benefits out of the tools.
Security education and training: More the attackers are expanding targets on businesses, awareness education is critical to prevent ransomware infections. We recommend establishing training programs for employees to recognize common social engineering tactics and also include OAuth abuse scenarios in these programs are important.
Incident response readiness: Offensive security practices contribute to an organization's incident response preparedness. By conducting red team exercises or tabletop simulations, organizations can test their incident response plans, identify potential weaknesses, and fine-tune their response procedures. Training methods like Purple teaming is designed to test monitoring and incident response process by collaborating with external offensive security professionals. War gaming is another valuable training to test an organization's incident response and gain insights into an organization's ransomware readiness. These exercises support not only for security team but also business leaders and key stakeholders to be clear on their role during a major incident and be ready to respond swiftly to the incident.
Continuous improvement: By regularly conducting security assessments and penetration tests, organizations can continuously implement patches and updates, enhancing network segmentation, and strengthening security controls. It is important to have an elaborated analyze of the assessment findings and define remediation action plans. Systemizing ongoing improvement reduces the likelihood of successful ransomware attacks.
Overall, offensive security practices play a crucial role in the prevention and mitigation of ransomware attacks. By adopting these practices, organizations can stay one step ahead of attackers, identify vulnerabilities, improve their security defenses, and minimize the potential impact of ransomware incidents.
If you would like to discuss more on the proactive cyber practices for ransomeware resilience, please contact us.