Securing 5G, advanced connectivity, and edge has been saved

Perspectives
Securing 5G, advanced connectivity, and edge
Why evaluate your network security posture now—and how
As organizations embrace enterprise 5G, advanced connectivity and edge, and as digital transformation scales new heights, opportunities for bad actors to unleash increasingly damaging cyberattacks increase exponentially. It is time for businesses that have embarked on their network transformation journeys to strengthen their network security and align their solutions with industry cybersecurity standards, regulations, and guidelines.
Fast-forward to the future of connectivity
The future of connectivity increasingly requires organizations to conduct open architecture assessments to highlight security areas that need improvement, enhance user experience, improve network performance, and align with cybersecurity standards, regulations, and guidelines. Diverse network technologies and use cases will require varying levels of monitoring and information correlation. Organizations need to probe, understand, and correlate various types of traffic to protect their networks.
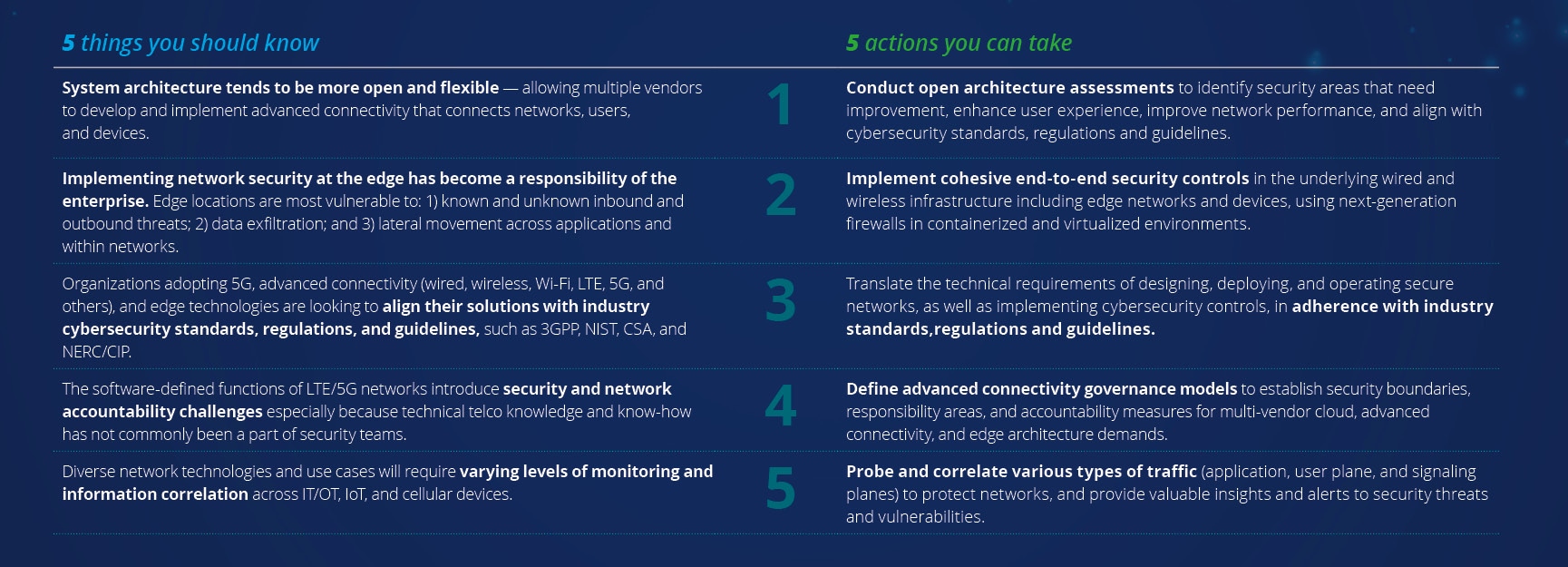
How ready is your organization?
Is your organization ready to make strides toward securing 5G, advanced connectivity, and edge while also upgrading network security capabilities and threat identification mechanisms? In our 5x5 series: Insights and actions, we explore what organizations should know and the actions they can take today. Download the report now.
Get in touch
Ally Adnan |
Shehadi Dayekh, PhD |
James Lee |
Recommendations
Take 5: 5G cybersecurity
Part of the Take 5 on 5G article series
Understand the market: The advanced connectivity and edge computing revolution
Tapping into the power of Connected Edge opportunities

