Article

Future of Control | GRC & ERP Technologies: Intelligent Access Risk Management and Control
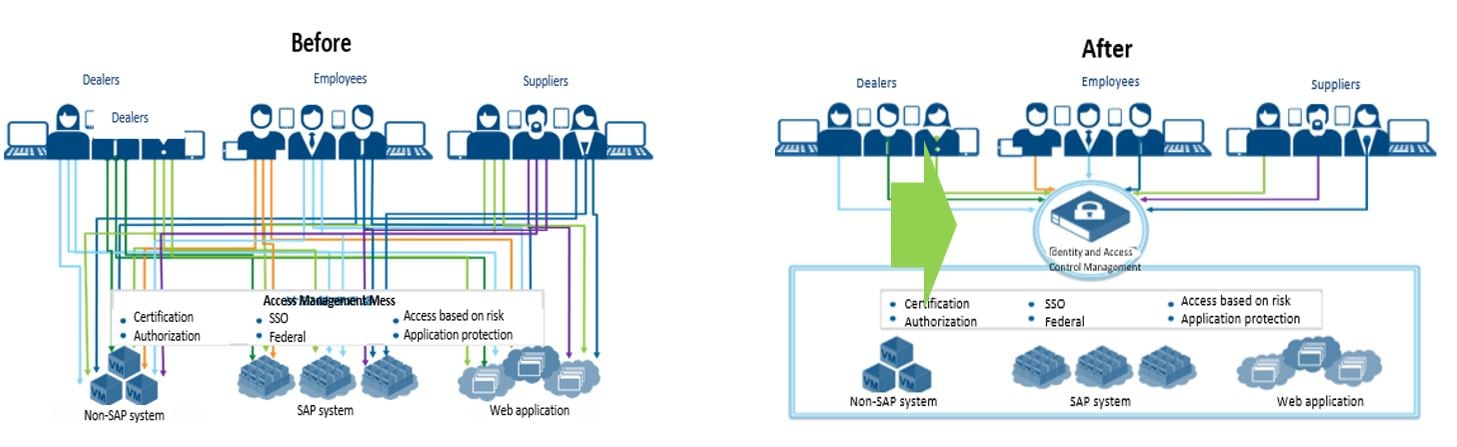
Intelligent Access Risk Management and Control Solution from Deloitte focuses on access risk monitoring and management, privacy protection and transaction protection in the process of digitalization, which is not only an effective foundation for security management and control, but also an important component of our vision for the Future of Control.
Challenges for Digital Access Risk Management and Control
Internal
- Large businesses run a range of application systems, which involve various categories of sensitive data, such as information related to customers, price, R&D and so on. The increased flow of data has exacerbated the data security challenges that enterprises face.
- Inappropriate or insufficient access control may bring negative impacts and losses which are difficult to predict and estimate for enterprises. It could also result in significant financial impact caused by the leakage of sensitive information or reduced control over company property and funds.
External
- External environment: Current domestic and international market environment is complex and changeable, such as China-United States trade tensions, Brexit, etc., increasing cybersecurity risks;
- Regulatory policies: Recently, a series of laws and regulations regarding risk compliance have been issued in China, such as the Cyber Security Law, the E-commerce Law, the Data Security Law (Draft) and Personal Information Protection (Draft), to standardize the criteria and requirements related with risk control. Internationally, various countries are also gradually introducing relevant laws and regulations regarding risk control and compliance, such as the European GDPR, and India is also about to introduce a personal information protection law.
Based on a domestic and international analysis of six years of internal control compliance data for listed companies, it was found that 5 of the top 12 control deficiencies existed in the enterprises were related to user authorization and access control.
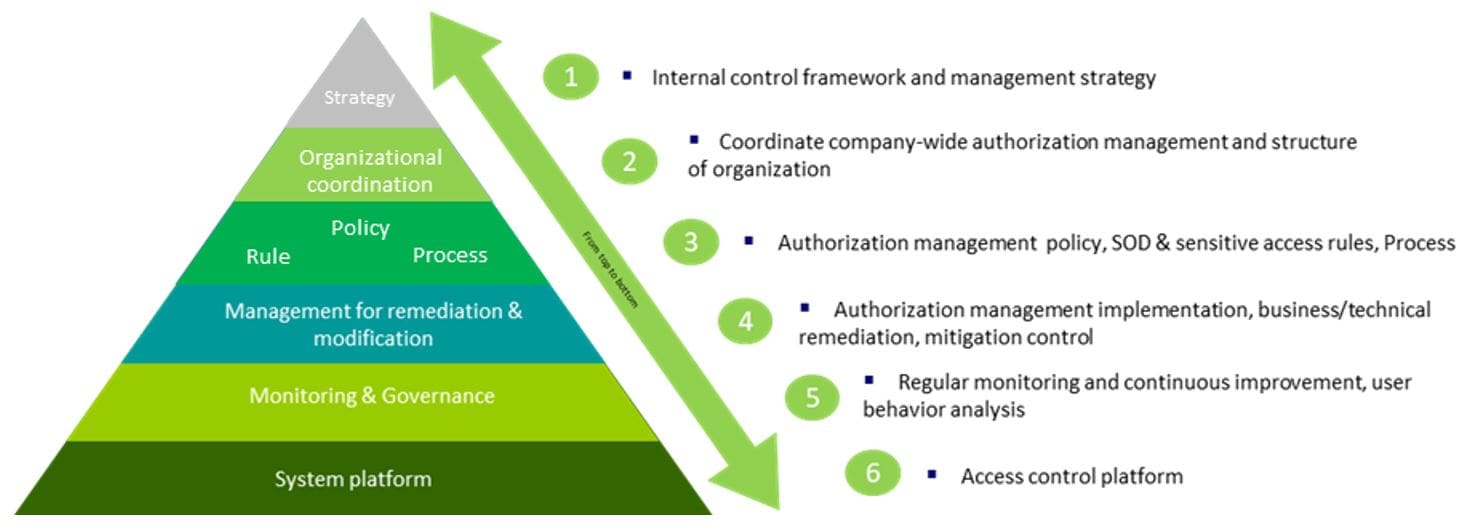
Governance Structure for Digital Access Risk Management and Control
Based on years of best practice, Deloitte proposes a six-layer model for digital access risk management and control governance:
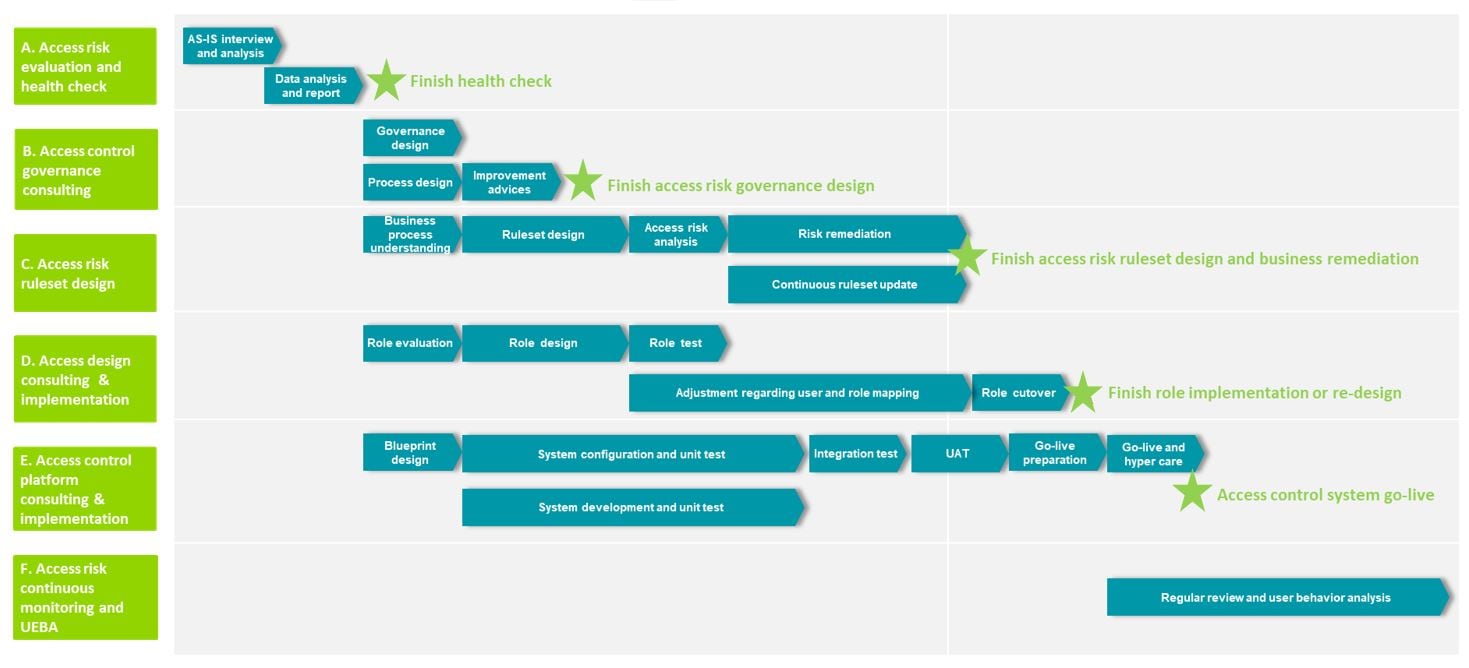
Roadmap for digital access risk management and control
Intelligent Access Risk Management and Control Solution from Deloitte
Deloitte provide clients with the following six types of service:
- Access risk evaluation and health check
- Access control governance consulting (Policy/Organization/Process)
- Access risk ruleset design ( SOD & Cortical Access)
- Access design consulting & implementation (Implement/Re-design, SAP S/4, Self-developed systems)
- Access control platform consulting & implementation (SAP GRC, Deloitte access control platform and so on)
- Access risk continuous monitoring and UEBA
Value for digital access risk management and control
Improve business efficiency and cut cost
- Reduce expenses on user account management and service desk operation
- Strengthen user life cycle management efficiency and access control process
- Reduce management cost through self-service and commission
- Use workflow to improve control and accountability for business leaders and manager approvals
Improve user experience
- Increase productivity through accessing business applications quickly with SSO
- Reduce the number of accounts and passwords to improve user experience
- Customers can conveniently access applications and traditional system of enterprise
- Business leaders and managers use a unified interface to process access requests, reviews and approvals
Governance and security benefits
- Reduce the risk of unauthorized access to critical systems
- Consistent management and automated enforcement of security policies and access controls
- Defend against unscrupulous user accounts
- Reduce the risk of data loss and privacy-related incidents and breaches
Meet compliance requirements
- Real-time views and reports to clearly understand usage of permissions
- Helps meet compliance checks for internal security policies and government regulations
- Improve accuracy and accountability regarding regulatory compliance
- Manage privileged access and separation of duties (SOD) controls
Business driven and IT agility
- Integrate identities of partners and suppliers to create business synergies
- Support current mobile, social, cloud-based business environment
- Simplify customer registration and application access process to enhance customer experience
- Automated role-based access to business applications