
Applying commercial intelligence to counter weapons of mass destruction Exploiting underutilized commercial data sources can enhance actionable intelligence in an evolving threat environment
8 minute read
13 November 2020
As weapons of mass destruction threats evolve, using traditional tools to detect malicious activity may not suffice. Analysts can turn to commercial intelligence methodologies to enhance intelligence efforts.
In May 2019, the United States seized a North Korean–flagged cargo vessel.1 During the previous year, the Wise Honest ship had attempted to transport 25,500 tons of coal from North Korea to international purchasers. The US government’s complaint against the Wise Honest detailed the ways North Korea used the vessel to violate US and United Nations sanctions designed to counter the proliferation of weapons of mass destruction (WMD).2
Learn More
Explore the Government & public services collection
Learn about Deloitte’s services
Go straight to smart. Get the Deloitte Insights app
The US complaint revealed that American banks had unknowingly facilitated transactions in US dollars that paid for services and equipment for the Wise Honest, thereby violating domestic laws and international sanctions pertaining to WMD development.3 However, these banks did not intentionally help the Wise Honest; they simply got lost in the complexity of modern financial transactions—a labyrinth of countless actors transacting worldwide in near-real time. The fact that these banks were not aware of the violations demonstrates the difficulty of identifying such activities.
The Wise Honest case is one example that demonstrates how nefarious actors can exploit the complexity of commercial and financial systems to fund state-supported weapons programs.4 With the right tools and know-how, however, the increasingly digital nature of trade and commerce can support solutions to counter illicit activities, especially WMD proliferation. By leveraging next-generation commercial data analytics, supply chain risk management, human capital transformation, and other commercial intelligence methodologies, the United States, its allies, and partners can expand strategies to better understand and effectively counter WMD threats. (For the definition of commercial intelligence, see sidebar, “What is commercial intelligence?”)
What is commercial intelligence?
Commercial intelligence refers to intelligence gleaned from open-source, commercial, and proprietary data sources from all over the world. It is published in English and foreign languages, capturing data from sources such as business ownership records, shipping information, litigation filings, and international and regional news media. It can be exploited by practitioners with extensive due diligence experience in the mergers and acquisitions, banking, and financial sectors.
Navigating a complex commercial and financial environment
The ability to purchase items from all over the world with one click of a button, and to track shipments of goods in real time, are just two examples of the benefits derived from the complex and data-driven nature of commercial and financial transactions. This complexity is supported by the volume of commercial data available and the myriad international and technological venues where these financial transactions take place.
It is estimated that from 2018 to 2024, the digital payments market, such as online purchases, mobile banking, and cryptocurrencies, will double due to smartphones and online banking applications.5 These digital payments travel through international, technology-driven supply chains—traversing multiple legal jurisdictions—and create digital exhaust from an ecosystem of international suppliers, customers, regulators, and other actors.6 While devices and digital venues support modern commerce, they, unfortunately, also can be used to unintentionally aid malignant actors.
While devices and digital venues support modern commerce, they, unfortunately, also can be used to unintentionally aid malignant actors.
Address evolving WMD threats: Traditional tools only go so far
WMD development and proliferation occurs in an increasingly complex operating environment. The same venues that facilitate legal global business and spur economic growth can also be utilized by illicit actors. In addition to using circuitous trade routes to ship goods, money, and illegal materials, proliferators use digital financial transactions, cryptocurrencies, and newly established, sometimes one-time-use front companies to circumvent authorities and finance WMD proliferation.
These activities can result in “clean” entities or entities less likely to be monitored through traditional counterproliferation approaches (sanction lists), or national technical means (satellite monitoring) being involved, unwittingly, in illicit transactions. Such methods of obfuscating identity increase a WMD proliferator’s ability to evade detection, boosting the probability of success. In times of crisis, such as the COVID-19 pandemic, proliferators may seek to take further advantage of shifting national attention, supply chain disruptions, and resource challenges to continue undetected development and proliferation of WMD or related materials.
Traditional tools for countering WMD may not suffice in this modern environment. Traditional intelligence disciplines (INTs) include human-derived intelligence, signals intelligence, imagery, and intelligence derived from physical properties of a system, such as chemical or electromagnetic emissions. These traditional INTs can be successful in capturing certain types of relevant WMD information, such as the qualitative descriptions of the status of a nuclear program, phone or email communication between a proliferator and a buyer, or the construction of new missile silos.
Open-source intelligence (OSINT), such as information obtained from data freely accessible online or via some commercial providers, is also used by the intelligence community (IC).7 Historically, however, the IC has focused on OSINT related to social media monitoring and foreign language media outlets.8 Commercial intelligence analysts exploit additional sources to enhance the intelligence picture, including corporate records, bills of lading, business ownership records, and analysis of other business transactions (figure 1). These commercial intelligence tactics can be further enhanced with purpose-built data analytics platforms that utilize the large amount of data produced by financial exchanges to capture data trails left by commercial transactions.9
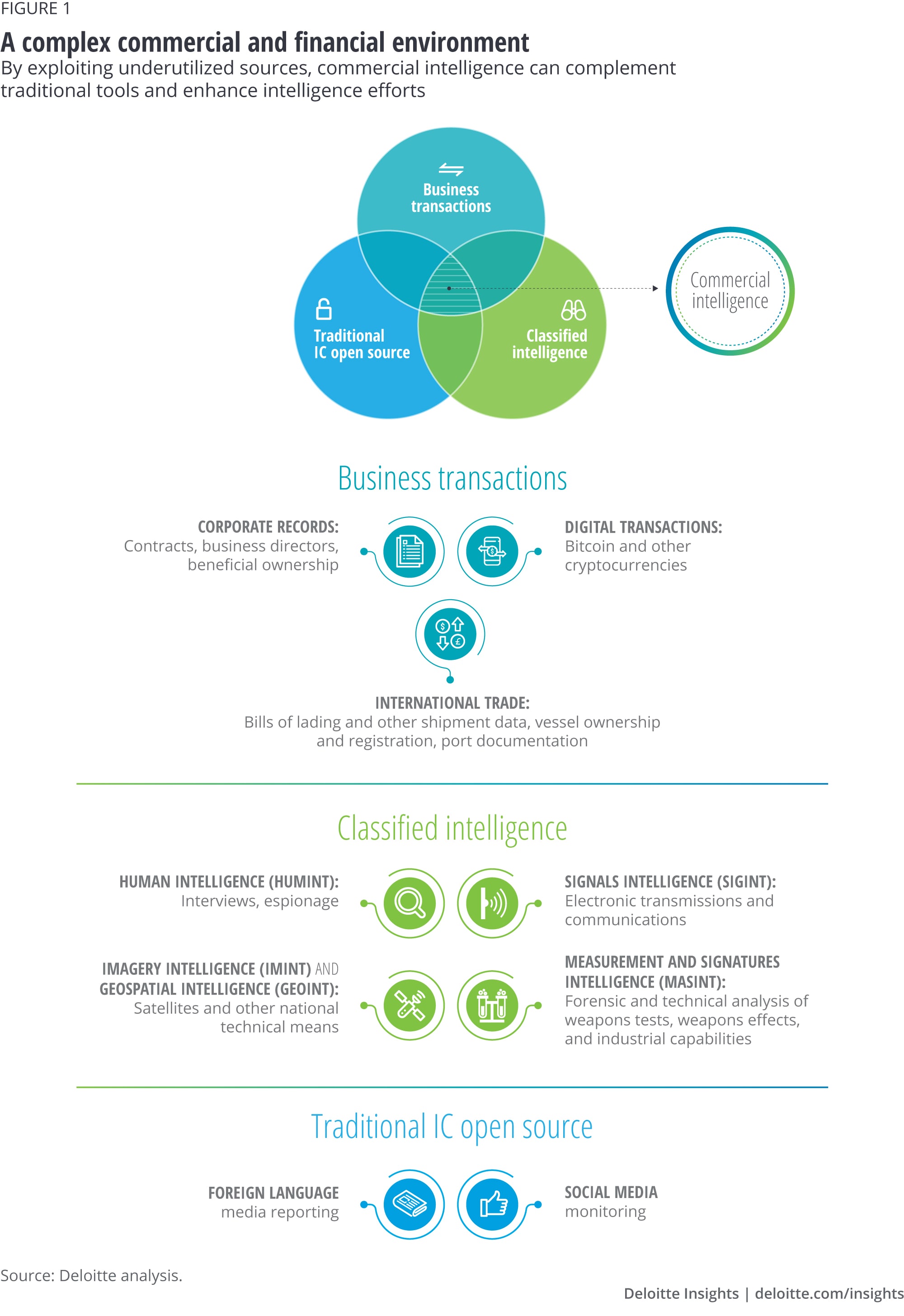
Intelligence analysts are typically inundated with vast amounts of data that could potentially drain time and resources.10 New commercial intelligence methodologies aimed at quickly collecting, distilling, and assessing large amounts of unclassified, open-source data can effectively use large amounts of data, eliminate information silos, and provide a clearer analysis to support the detection of malicious activity.11
Leveraging commercial intelligence to thwart WMD risks
Advanced commercial intelligence methodologies can supplement traditional IC tools to produce more actionable intelligence. Because commercial intelligence is unclassified and easily shareable, it can support a government’s countering weapons of mass destruction (CWMD) mission by producing a clearer analysis across national security agencies and with foreign partners. Commercial intelligence is also incredibly useful for lead generation, providing necessary details and identifiers that allow more efficient use of classified intelligence tools and assets. In particular, CWMD stakeholders can utilize commercial intelligence–driven solutions in three key areas: data analytics, supply chain risk management, and human capital transformation. Here’s what they can consider:
Identify areas where commercial intelligence can augment existing CWMD methodologies
Data analytics methodologies and tools can help agencies identify WMD proliferators and illuminate weapons networks. Commercial intelligence relies on unclassified data that is not widely accessed because it often resides in commercial and proprietary databases. Key financial transaction data may be accessible only through corporate ownership records, financial disclosures, and court filings that may require paid access and specialized knowledge to identify anomalous behavior.
Commercial intelligence analysts apply expertise in corporate records and business transactions to map relationships between individuals and business entities, collecting unique identifiers (names, emails, phone numbers, addresses) and identifying points of influence in a network. In the case of the Wise Honest, investigators were able to build the legal case utilizing Automatic Identification System (AIS) data and bills of lading that pointed to sanctions evasion activities.12 Other transportation data that can expand the intelligence picture include vessel travel histories, Harmonized Commodity Description and Coding System (HS) code numbers, ship identifiers, and port documentation. The quantity of data can be overwhelming—in terms of maritime trade alone, there are more than 3,600 cargo vessels that have traveled between China and the United States in the past year.13
Commercial analysts understand access requirements and use a range of tools to collect and interpret the vast quantity of data. Data scraping and social media analytics tools can be leveraged to gather further information. Artificial intelligence (AI) and machine learning (ML) tools can help sift through data for key markers. After the information is analyzed, next-generation visualization tools can bring insights to life through network mapping, simulations, and graphical data representation to support a more complete intelligence picture.
Adopt supply chain risk management practices to enhance CWMD missions
Risk management can support the US government’s efforts to analyze and mitigate WMD development and proliferation in supply chain ecosystems. Supply chain risk management methodologies typically use commercial intelligence to map supplier networks and identify and mitigate risk. Those same supply chain risk management tools can be applied to CWMD missions seeking to analyze an adversary’s WMD supply chain and identify points of vulnerability and opportunities for interdiction.
Network mapping can enable better monitoring of dual-use goods that have civilian and military purposes to potentially create a WMD. Expert vendor vetting by supply chain analysts can be key to understanding sublevel supplier networks of goods, equipment, or services. For example, when illuminating the supply chain for a foreign government’s weapon platform, a cursory look may correctly identify the primary manufacturer that provides the system to the government. However, research by Deloitte teams has found that public procurement records, media reporting, and trade data can reveal multiple additional subtier suppliers, widening the network to dozens of involved companies and hundreds of individuals. Any one of these can be a witting, or unwitting, vector for WMD proliferation. Through network illumination and supply chain pattern identification, commercial intelligence analysts can find supporting open-source and commercial data to highlight specific facilitators, front companies, and supply chains used for suspicious transactions, and potential sale of dual-use items, destined for the sanctioned regimes. Commercial intelligence can be key to identify procurement or transportation of materials that violate WMD proliferation sanctions across the globe.
Additionally, as warehouses, factories, and ports increasingly implement Internet of Things (IoT) solutions, more data will be generated and could provide greater insights into inventory anomalies. Increased supply chain transparency supported by commercial intelligence and expertise could enable faster, agile responses to detect WMD development or proliferation activities.
Invest in the workforce to build strong commercial intelligence apparatuses
Human capital transformation can help the US government realize the full potential of robust commercial intelligence and address evolving WMD challenges. Commercial intelligence requires tailored expertise with specific data sources, methodologies, and tools available in the market. Analysts will increasingly need technical knowledge in the commercial space, especially to identify anomalous behavior or abnormal business practices involved with global transactions.
Analysts in this field may have skills that include big data analytics, global trade evaluation, industry analysis, commercial data investigations, and native language capabilities. These skills can be combined to provide helpful commercial data pertaining to CWMD. Corporate records are often created and maintained at a regional level. As a result, there are more than 500 different websites globally that can be used to identify and validate beneficial ownership, each uniquely suited to different investigative targets.14 Even with the aid of aggregators, analysts need to understand the intricacies of the primary sources and search in the local language to identify the relevant record. Analysts must possess the knowledge of where relevant data is located, how to procure the information, and what data would be valuable.
Analysts must also have the capability to assess the collected data and accurately distinguish between real and doctored or falsified information. These commercial intelligence skills can be applied to track down court records in foreign jurisdictions to find additional identifiers, scan foreign language social media feeds, or follow ownership in offshore jurisdictions.
A culture within the IC that ambitiously invests in OSINT as an integral component of all-source reporting can be critical to creating an effective commercial intelligence capability on par with other classified INTs. The US government can support this culture by investing in resources and attracting top talent to support a robust commercial intelligence capability necessary for CWMD efforts in the digital age.
As WMD development and proliferation threats continue to evolve and diversify, governments will need novel solutions to protect citizens and national interests. Commercial intelligence offers a valuable addition to the CWMD toolbox—purpose-built for a world in which the amount of newly generated data is exploding annually. Government agencies responsible for CWMD can use these emerging capabilities by:
Commercial intelligence offers a valuable addition to the CWMD toolbox—purpose-built for a world in which the amount of newly generated data is exploding annually.
- Identifying areas where commercial intelligence can augment existing CWMD methodologies. Data analytics methodologies and tools can help agencies identify WMD proliferators and illuminate weapons networks. Those same tools can support response efforts in the event of a WMD incident, helping to digest real-time reports, determine casualties, inform personnel tasked with decontamination, and monitor follow-on developments.
- Adopting supply chain risk management practices to enhance CWMD missions. Supply chain network mapping and vendor vetting can ensure the dependability of CWMD countermeasures and equipment, as well as support US government efforts to analyze and mitigate WMD development and proliferation.
- Investing in the workforce to build strong commercial intelligence capabilities. Human capital transformation including the development of new career tracks, rigorous training, and tradecraft development can help the US government maximize commercial intelligence and meet the challenges of the evolving WMD environment.
Commercial intelligence analysts can utilize unclassified open-source data along with advanced AI and ML tools to provide clearer intelligence pictures and counter evolving and dynamic WMD threats. But investment in data analytics tools, risk management methodologies, or workforce transformation will likely only be successful if accompanied by a cultural transformation that begins to value the contribution unclassified commercial intelligence can make to existing CWMD efforts. Utilizing commercial intelligence effectively can enhance the US government’s ability to escape from the modern maze of commercial transactions and protect its citizens and allies from WMD threats.
More from the Government & public services collection
-
Seven lessons COVID-19 has taught us about data strategy Article4 years ago
-
Job-centric upskilling Article4 years ago
-
Child support’s integration imperative Article4 years ago
-
Planning a new presidential term amid growing uncertainties Article4 years ago
-
Envisioning transportation in a post–COVID-19 world Podcast4 years ago
-
Surviving the pandemic budget shortfalls Article4 years ago



















