Zero Trust strategy insights has been saved

Perspectives
Zero Trust strategy insights
Never trust, always verify with a Zero Trust security model
In this era of evolving business models, shifting workforce dynamics, cloud adoption, and increased device and connectivity complexity, many organizations are prioritizing the adoption of the Zero Trust security model. A Zero Trust strategy for cybersecurity provides the opportunity to create a more robust and resilient posture, simplify security management, improve end-user experience, and enable modern IT practices. Zero Trust by Deloitte offers a broad range of advisory, implementation, and managed services to help organizations align to the ‘never trust, always verify’ cyber approach while securing the ubiquitous nature of their modern enterprises.
Zero Trust Access
Deloitte’s Zero Trust Access service (ZTA) can help accelerate an organizations’ adoption of Zero Trust by securely connecting what matters most: users to applications. The service is designed to help businesses address the evolving requirements of enterprises to confidently protect their applications, infrastructure and data. It offers a cloud-native service that secures communications between end user devices, and enterprise applications, wherever they may reside. Deloitte’s Zero Trust Access can replace legacy remote access technology with a modern Deloitte managed service or complement a broader ecosystem of technologies and capabilities to accelerate Zero Trust adoption.
With innovative microcontainer-based data protection, the Zero Trust Access service enables organizations to protect sensitive information, prevent data exfiltration, and potentially replace costly and complex legacy solutions. The service provides a turnkey solution that accelerates Zero Trust connectivity with application segmentation and inherent data protection capabilities – relieving IT and security teams of the cost and complexity that’s typically associated with deploying and maintaining a myriad of security controls to achieve similar outcomes.
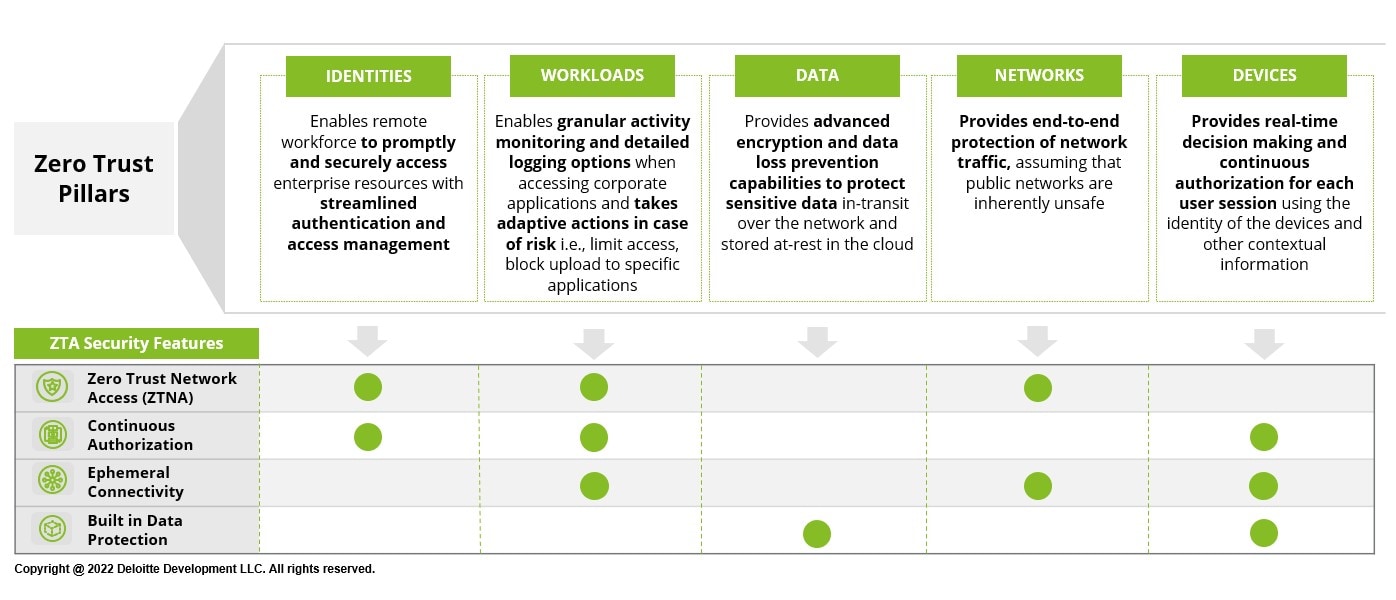
Additional features of the service and their applicability to the core pillars of Deloitte’s Zero Trust framework are depicted below:
- Zero Trust Network Access (ZTNA) - Software defined perimeter (SDP) architecture, coupled with application segmentation capabilities, removes the need to provision inbound network access to sensitive resources. Connecting users directly to target applications vs. broad network access prevents lateral movement risks by making the underlying networks inaccessible to the user.
- Continuous Authorization - Authorization is continuously re-examined after initial access and can be dynamically adjusted based on contextual security information such as device security posture, location, time of day, and device integrity.
- Ephemeral Connectivity - The cloud component brokers each connection and tears it down upon session completion. Peer-to-peer (P2P) communication between the end user and target application allows for data traffic to flow directly between the source and destination, rather than traversing third party environments - virtually eliminating man-in-the-middle threats.
- Built-in Data Protection - Data at-rest, in-use, and in-transit is secured through strong encryption, configurable control over print/copy/paste features, anti-keylogging, anti-screen scraping, watermarking, remote data destruction, and other built-in data protection features.
- Identities are the new “perimeter”—a core component of any Zero Trust architecture is shifting to identity-based access control decisions based on user profile, entitlements, authorization, and acceptable usage patterns. Telemetry & analytics as well as automation & orchestration can be considered over-arching domains that stitch the underlying pillars together.
- Workloads are applications or services people use, either on legacy infrastructure or in cloud environments and containers. Workloads can be hardened, segmented, and monitored on a granular level with adaptive actions, such as limiting access or blocking uploads to specific applications. The concept of DevSecOps - a transformational shift which incorporates secure culture, practices, and tools to drive visibility, collaboration, and agility of security into each phase of the DevOps pipeline - also fits into the Zero Trust concept. Applying such methods enable security controls to be baked into the fundamental design of each application and verified throughout the CI/CD (Continuous Integration/Continuous Development) process.
- Data lies at the heart of an effective Zero Trust strategy. Organizations need to understand what data they have, where that data is stored, who/what should be able to access that data, and under what conditions. It is therefore paramount that enterprise data be discovered, inventoried, governed, classified, and tagged in a manner that can be used to inform access control decisions. Data should also be protected through obfuscation, encryption, and advanced data loss prevention mechanisms at all stages – at rest, in use, and in-transit.
- Networks are the highways that are required to establish communication between users, devices, and workloads. Network controls should be implemented to block unintended / unauthorized network communications (segmentation) or device connections (network access control – NAC), inspect traffic patterns, and analyze network activity. Zero Trust security begins with the assumption that all network connection requests are inherently untrustworthy.
- Devices include both known and managed endpoints, unmanaged (e.g., Bring Your Own Device - BYOD) and smart devices (e.g., Internet of Things - IoT) that connect to an organization’s network and enterprise assets. Devices should be subjected to continuous assessment for risks and threats and to evaluate their compliance with the defined security policies. Access decisions should be based on device characteristics such as installed software, geolocation or installed credentials (e.g., machine certificate) and other contextual factors (e.g., time/date of the request, security posture of the device, browser information).
- Telemetry and analytics systems collect data from relevant security controls into a centralized platform for event correlation and advanced analysis that can detect suspicious and potentially malicious behaviors. Threat intelligence should also be integrated to enable a threat-driven security posture for the organization. As modernized controls are implemented, the associated telemetry should be ingested in order to enhance situational awareness of usage patterns.
- Automation and orchestration capabilities enable a more proactive security posture by automating detection, prevention, and response actions through integrated security controls. Security operations can become more productive when investigative tasks are automated in response to an ever-growing flood of security alerts. Integration of the organization's security systems allows for orchestration of pre-defined incident response activities in near real-time—not only to detect threats but also take action to isolate and neutralize them.
Zero Trust Fundamentals
A Zero Trust strategy brings with it a set of design principles that guide security architecture development and build on existing security investments and processes. To enforce access control, companies need to have situational awareness of their data and assets; companies that lag on basic cyber hygiene principles and practices may be challenged to realize the full benefits of Zero Trust. Fundamentals may include:
- Data discovery and classification. Data governance, inventory, classification, and tagging are critical. To create the appropriate trust zones and access controls, organizations need to understand their data, the criticality of that data, where it resides, how it is classified and tagged, and the people and applications that should have access to it.
- Asset discovery and attack-surface management. Many organizations lack a real-time, updated inventory of all IT resources—including cloud resources, IP addresses, subdomains, application mapping, code repositories, social media accounts, and other external or internet-facing assets—and therefore can’t identify security issues across the complete attack surface. To facilitate risk-based policy decisions surrounding their assets, it’s critical for organizations to understand the enterprise IT environment.
- Configuration and patch management. Without the ability to efficiently manage and document baseline configurations of key technology systems, deploy appropriate patches, test patched systems, and document new configurations, companies cannot easily identify changes and control risks to these systems. Malicious actors can exploit vulnerabilities to gain a foothold within an organization.
- Identity and access management. To ensure that access to technology resources is granted to the proper users, devices, and other assets, enterprises should federate, standardize and automate their identity life cycle management processes. They can extend their operations beyond traditional boundaries while protecting critical resources and maintaining an efficient user experience by moving the identity stack to the cloud, consuming identity-as-a-service (IDaaS), or implementing such advanced authentication methods as physical biometrics, behavioral monitoring, and conditional access.
- Third-party risk management. To fully understand their entire risk surface, organizations should seek greater visibility into cyber risks related to their supply chains and ecosystem partners, including suppliers to third-party vendors.
- Logging and monitoring. To identify potentially malicious incidents and issues, security teams need automated logging and monitoring systems with advanced artificial intelligence (AI) and machine learning (ML) capabilities can help simplify the process of tracking, analyzing, and correlating data from volumes of detailed logs as well as alerts generated by internal and external systems, security controls, networks, and processes.
Benefits of a Zero Trust security model
A Zero Trust architecture may help overcome common challenges of traditional cybersecurity approaches by leveraging new capabilities and opportunities to close gaps and become more agile and efficient. Potential benefits of Zero Trust include:
- Ubiquitous security. When users, devices, resources, and their related data are identified and isolated, intrusions that may occur can similarly be isolated to prevent lateral movement and limit the potential blast radius. Such an environment requires a high degree of automation and orchestration, resulting in a more secure, resilient, and integrated environment. This compares with a traditional, perimeter-centric approach to security where layered but siloed defenses can be pierced to expose the internal environment and potentially put the entire organization at catastrophic risk.
- Evasive target. The fully integrated, dynamic approach under Zero Trust can protect the organization regardless of where connections originate. This makes the organization more difficult to target than one whose infrastructure is easily identified by adversaries.
- Increased visibility. Analytics such as anomalous detection, machine learning, AI, and real-time data inventory and cataloging can enable organizations to gain broader, real-time visibility into their threat landscape. This deployment of active defense technologies can overcome the limited visibility that is common in organizations which identify threats only as they hit the perimeter.
- Predictive. Organizations can anticipate adversary movements and initiate pre-emptive action more proactively than with traditional defenses, which are more reactive in nature.
Resilient cyber podcast : Tune into an award-winning podcast series that features cyber leaders sharing insights into the evolving cyber landscape.
To learn more about Deloitte’s Zero Trust Access, get in touch with our Zero Trust leaders below.
Explore our Zero Trust insights
Recommendations
Quantifying cyber risk to chart a more secure future
Leverage the capabilities of CRQ to reveal and address cyber threats