Zero Trust adoption & implementation | Deloitte US has been saved
Authored by Tara Mahoutchian, Mike McLaughlin, Ali Thayres and Andrew Rafla
Introduction
In the hybrid working world, the demand for effective business collaboration necessitates a more agile approach to an organization’s cyber security. As a result, Zero Trust security architecture has been gaining momentum and attention in the post-pandemic world. A Zero Trust implementation is much more than a technological implementation, it is also a business and cultural transformation that is dependent on culture, communications, and awareness.
As organizations embark on their Zero Trust journey, a human-centered approach is critical to developing an effective cyber-centric future. The concept of Zero Trust is about removing implicit trust and comparing each connection request based on the authenticated and authorized user as well as other contextual signals (e.g., geolocation, device posture). To achieve adoption by employees, a Zero Trust implementation should account for the importance of a strong employer-employee relationship to mitigate the risks of resistance and business disruption.
This piece will focus on the culture, communications, and awareness component in the governance layer of the framework pictured below, applying a Human Capital Cyber Workforce Solutions lens to Zero Trust. A comprehensive Zero Trust implementation should address the elements below, including additional areas related to governance (architecture and operations), enablers (telemetry and analytics and automation and orchestration), and core domains (identities, workloads, data, networks, and devices).
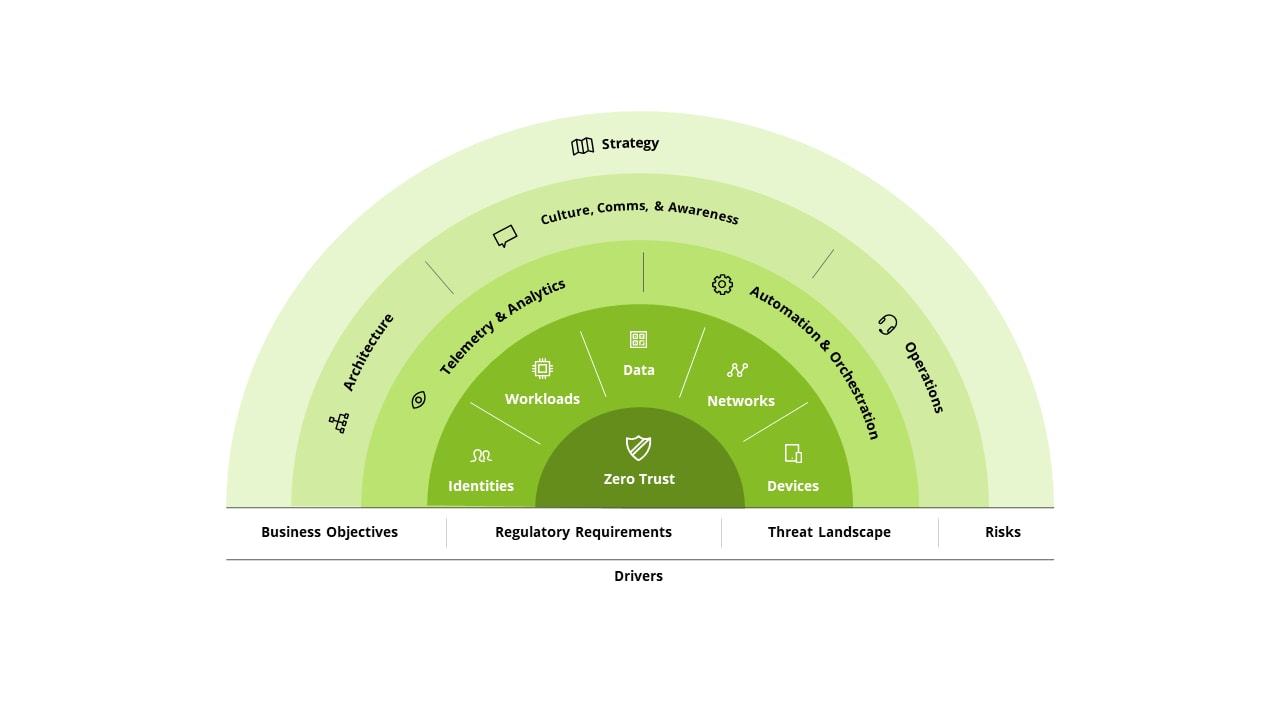
Critical Success Factors
There are three critical elements of an effective Zero Trust adoption by employees, which we’ll cover in detail in the following sections:
- Human Centered Approach to the program design
- Driving Leadership Alignment and Accountability
- Prioritizing a Diverse Talent Landscape
Focusing on the three elements above will help decrease disruption, support the organization in becoming more dynamic and adaptive, and empower employee productivity by reducing friction and improving user experience, all in pursuit of a more secure organizational posture.
As organizations across industries move their Information Technology (IT) and data operations to cloud-based platforms, cloud-native security solutions that are inherently scalable, resilient, and agile are essential for organizations looking to remain competitive. To fully realize the business benefit of a Zero Trust strategy, aligning leadership, reimagining the modern governance model, and understanding the value of a human-centered approach may be the difference between delivering a leading solution or a lackluster roll out resulting in high turnover and a weakened culture.
1. Human-Centered Approach to the program design: A Mission and A Strategic Change Plan
When embarking on a large-scale IT transformation, organizations sometimes develop tunnel vision and focus exclusively on the massive investment they may have made in the technology. However, as with many business transformations, taking a human-centered approach at the program design stage will help increase the likelihood that the organization is able to realize the full potential of their investment through focused employee adoption activities.
“Zero Trust is as much a cultural innovation as a technological one. Getting people to change their behavior requires communication and training. Zero Trust enables secure execution of innovation and business strategy; it’s crucial that everyone realizes the ongoing benefits of its deployment in supporting evolving digital transformation.”1
The success of a Zero Trust implementation will hinge on the speed of adoption among impacted stakeholders and whether they are able to take ownership of their constituents’ new ways of working. The first step in doing so is to develop a compelling employee value proposition that connects individuals to the greater vision and mission tied back to the organization’s long-term strategy. Coupling the articulation of an employee-focused vision and mission for Zero Trust with a comprehensive Organizational Change Management (OCM) Strategy that includes a timeline running parallel to the implementation milestones to support employees every step of the way, will give impacted users the knowledge and skills needed to embrace the change.
A compelling vision statement should be designed to mitigate the possible risk that employees feel they are being “kicked out” of the inner circle by their employer and no longer able to move freely once they have completed an initial VPN authentication. Program teams should identify creative ways to elevate the modernized user access patterns and engage employees as stewards of security and safety for the organization. Employees will no longer have “keys to the kingdom” once they log in via VPN, however, they are part of the collective effort to enhance the vigilance, security and resilience of the organization.
In addition, a strategic OCM approach anchored in our Transformation Intelligence Methodology, both agile and iterative in nature and customized for the complexity and challenges associated with cybersecurity implementations, is critical. One different challenge associated with a Zero Trust implementation is the shift in day-to-day operations for many employees that will require new ways or working.
Anchored in “Moments that Matter”, the approach should be tailored to each client, transparent about the ways in which Zero Trust could impact their workflow and include a roadmap of tailored interventions to determine end user readiness. To drive acceptance and adoption and allow the required flexibility to scale as needed along the implementation journey, project teams should remember that their people and mission are their north stars.
2. Driving Leadership Alignment and Accountability
A Zero Trust implementation is complex and will require support, investment, and buy-in from leaders across the organization to effectively safeguard the enterprises’ investment. It is critical for business leaders to establish clear business outcomes for a Zero Trust implementation, connect this vision as the north star for the whole organization, and take iterative and incremental steps towards that north star. As a specific component to a human-centered approach to the program design, developing a cohesive and compelling vision statement for the future of the organization should consider highlighting the business imperative of establishing a safer and more secure work environment.
Leaders should be willing to ‘walk-the-walk’ by investing in the upskilling required for their teams to understand potential risks and threats, and how Zero Trust will impact their user experience and associated access patterns. As subject matter specialists, the Chief Information Security Officer (CISO) and IT Team leaders should help recruit and develop business leaders across the organization as champions of the program to build awareness and excitement among their respective teams. By creating a culture of leadership alignment and accountability, leaders will have a strong change story to help bring their teams along and keep them focused on benefits of future-proofing the organization with a strong security infrastructure. These types of transformations can be used to elevate the company’s brand and positioning with prospective employees and constituents.
3. Prioritizing a Diverse Talent Landscape
As organizations continue to grapple with talent issues following the “Great Resignation,” embarking on a cybersecurity transformation should include cultivating a diverse talent landscape. With more digital natives entering the working world, the cyber workforce is becoming increasingly diverse. Gen Z is the U.S.’s most racially and ethnically diverse generation and is on its way to becoming the best educated generation in U.S. history.2
Talent diversity is essential for an organization’s cyber capabilities and the Zero Trust journey. Studies have shown that diverse teams perform better overall, are able to develop fresh business perspectives and can creatively problem-solve more effectively. While this finding is not to the cyber workforce, when talking about novel problems like the ongoing threat of new cyber-attacks, with no real roadmap for success, a team that celebrates diversity of thought and experience may be better able to understand and detect the mindset of cyber threat actors, and anticipate and mitigate complex cyberattacks, especially while working remotely.3
As skills evolve, human capabilities such as creativity, empathy and teaming endure. As we increase our talent diversity, the diverse workforce will be able to bring in these lasting human capabilities in effective and new ways to meet the demands of the market.4 In order to meet the needs of a diverse cyber workforce, IT executives and technology leaders have an important role in building inclusive cultures that foster engagement and collaboration.5
These needs also underscore the importance of feeling a sense of belonging. When entering a traditional field like cybersecurity, where leadership can be demographically different than newer employees, retaining them means not only valuing their creativity, but also making them feel a part of the organization. Recent statistics show that only 24% of cybersecurity workers identify as women, 9% as Black and 4% as Hispanic. Women and people of color are less likely to serve in leadership positions in cybersecurity companies, and there are stark cybersecurity salary discrepancies across race and gender.6 Part of human-centered messaging and internal marketing for large-scale transformations like Zero Trust should focus on two themes to help mitigate these issues:
- Zero Trust affects everyone in the organization, from CEO to the newest hire, and even the extended workforce. At its core, Zero Trust is about protecting sensitive data (e.g., client information, employee Personally Identifiable Information (PII), intellectual property, etc.) while modernizing security infrastructure to be competitive in the future
- Adherence to the new security protocols is a leading practice that bolsters the brand, creates a more secure and resilient enterprise, and ultimately enhances consumer trust. It’s an opportunity to get ahead of the competition and gives employees new skills they can use, whether they stay or seek employment elsewhere
What’s Next
As companies across many industries consider the potential of a Zero Trust security strategy for their organization, it is critical to balance the need to provide a secure and accessible IT ecosystem that supports the evolving needs of employees while enabling the agility and scalability to remain competitive in the market. A effective culture, communications, and awareness campaign should help employees understand that Zero Trust is a commitment to their safety, security, and flexibility.
While Zero Trust adoption may be a major transformation for many organizations, managing this change with a human-centered approach will fundamentally differentiate an effective implementation from a potential failure. When implementing Zero Trust architecture, carefully crafting the project branding from the outset is critical. Establishing leadership alignment to drive the program messaging is a cornerstone in building a culture of trust. Fostering a culture of diversity and inclusion to facilitate innovation and creative thinking empowers employees to take part in the evolution of the organization. Lastly, having leaders and strategic business partners from across the organization facilitate and take ownership of sustaining the changes required will result in the business realizing the full potential of the Zero Trust concept.
Together, C-Suite leaders can rethink the way they engage with key stakeholders across the organization, and how they work together and collaborate across Human Capital and Technology to fully realize the business benefits of Zero Trust. Executing a culture, communications, and awareness plan should be an integral part of any organization’s Zero Trust journey.
Authors:
Contributors:
- Norah Nicholls
- Jerry Peruchini
- Rozi Xu
- Davey Salwan
References:
1. The Future of Cyber Survey | Deloitte US
2. Generation Z is the Most Racially and Ethnically Diverse Yet | NPR
3. Cybersecurity and women: A call for diversity | Deloitte
4. The future of work and importance of human capabilities | Deloitte Insights
5. Diversity and inclusion in tech | Deloitte Insights
6. Building a More Diverse Cyber Industry | The Aspen Institute

