Digital risk management and controllership: The three pillars has been saved

Perspectives
Digital risk management and controllership: The three pillars
DRM and the role of the Controller: Part one
Digital transformation of controllership, finance, and organizations as a whole is moving into the landscape with a brute force that can create chaos if companies are not prepared. Even with proper preparation, the introduction of emerging technologies introduces risks to security, infrastructure, compliance, and governance. Managing these risks with a system of controls can be a significant indicator of an effective implementation, not only in the initial phases, but on an ongoing basis to help increase value and the return on investment (ROI) of automation.
June 8, 2018
A blog post by Julie Velayo, principal, Deloitte & Touche LLP
The inception of digital transformation has prompted organizations to ask specific risk-related questions about emerging technologies. How does this software change my financial reporting processes? How does this impact my controls? How will I know if I've impacted my compliance obligations? How will I manage a digital workforce in my controller's organization?
When shifting to digital, many organizations move to implement new technologies swiftly without giving full consideration to the various risks involved or taking the time to ask the questions that arise with each new digital solution. Even as the introduction of new technology into organizational environments continues to bring new risks, controls to mitigate these risks should also continue to progress.
Proper digital risk management (DRM) can benefit those looking to answer specific risk-related questions and create an organized structure around the control of those risks, even as they expand and progress. DRM is a framework and strategy designed to help companies govern risk associated with the end-to-end life cycle of digital transformation involving advanced technologies. DRM can help organizations enhance controls while increasing ROI and protecting value.
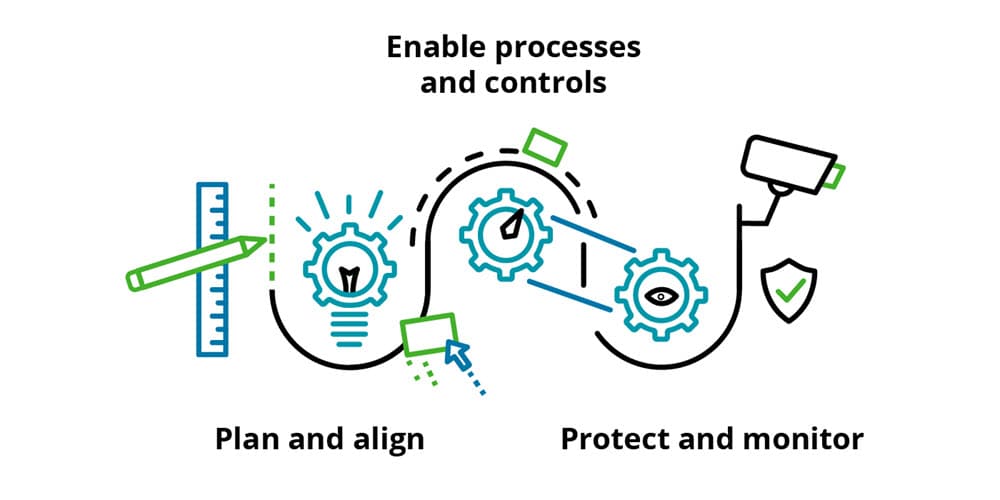
The DRM framework consists of three main pillars—plan, enable, and monitor—and it lays out a structure of risk management that may assist controllers and finance professionals as they navigate ongoing digital transformation challenges.
Embracing a DRM strategy may also bring significant benefits, such as:
- Improved compliance and governance that mirrors new technologies
- More efficient oversight of financial processes
- Potential cost reductions related to processing time and error resolution
- Scalability as new technologies are implemented and utilized
- Increase in automated controls
- Reduction in testing hours associated with manual controls

Three pillars of digital risk management
Plan and align: Laying the foundation for DRM
The first pillar of DRM involves planning and alignment around the structure that enables digital transformation—laying the foundation for the management of digital technologies and their associated risks.
This includes opportunity analysis, risk assessment, organizational redesign, designing a Center of Excellence for ongoing risk management, and developing a business case around emerging technologies.
Process and controls: Designing the structure for DRM
Digital transformation requires structured processes and procedures as well as a design for implementation and change management. The second pillar of DRM focuses on putting proper processes, controls, and policies in place to enable rapid transformation while maintaining effective risk management and mitigation.
In addition to processes associated with new technology, it is also imperative to design and organize the workforce elements of digital change within the second pillar of digital risk management. Creating protocols around training and culture, including a framework for the creation of a digital workforce, brings focus to the human element of transformation, not just the technology.
Protect and monitor
Digital transformation requires new approaches to traditional areas such as audit, compliance, and cyber, and methods for new areas such as brand and reputation management and algorithmic risk. Some questions that can be considered include: How will my audit change? How do I need to think about cyber differently? How will automation affect controls? How will a digital controllership monitor compliance?
The third pillar, the framework to protect and monitor digital risks, focuses on the new and ongoing protections to put in place around compliance, cyber protection, reputation, and crisis management. These regulatory and protective policies not only assist with the digital transformation but also help carry an organization through what may become a predominately digital function in the future.
Implementing the three pillars of the DRM framework can enable clear ownership of implementation and transformation activities across the digital space, helping to define the creation of a DRM Center of Excellence. Stay tuned for an in-depth overview of how to create a Center of Excellence for DRM and the value controllership can bring.
Visit the Controllership Insights blog for additional blog posts.
This publication contains general information only and Deloitte is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or other professional advice or services. This publication is not a substitute for such professional advice or services, nor should it be used as a basis for any decision or action that may affect your business. Before making any decision or taking any action that may affect your business, you should consult a qualified professional advisor. Deloitte shall not be responsible for any loss sustained by any person who relies on this publication.
Recommendations
Accounting automation and the future of controllership
Diving deeper into the benefits of new technologies