Third-party reporting proficiency with SOC 2+ has been saved

Analysis
Third-party reporting proficiency with SOC 2+
SOC2+ reports and the focus on trust services criteria
As organizations outsource more of their core operational functions, there’s been a large increase in demand for system and organization control (SOC) 2 reports. Enhanced SOC 2 reports, also called SOC 2+, are now in particular demand.
Explore content
- Download the report
- System and organization control 2+ reports
- Journeying from SOC 2 to system and organization control 2+
- Rapidly gaining traction
- Get in touch
An integrated system and organization control approach gains traction
Doing business as an “extended enterprise” is now the norm. Today, companies of all sizes routinely rely on an ecosystem of service organizations to carry out a wide array of functions, many of them mission-critical. Through these loosely coupled networks of third parties, companies have been able to vastly expand their reach and capabilities, often extending around the world to create new and exciting market opportunities.
Simultaneously, their increasing reliance on service organizations is fueling concern over greater enterprise risk exposure—especially since the third-party risk is difficult to identify, manage, and monitor. For service organizations, this translates into increasing customer demand for system and organization control reports. These third-party assurance reports help service organizations build confidence in their service delivery processes and controls through the attestation of an independent certified public accountant.
Most organizations are familiar with both SOC 1 and SOC 2 reports. While SOC 1 reports cover internal controls over financial reporting (ICFR) and support a customer’s financial audit, SOC 2 reports focus on the controls that are relevant to the following Trust Services Criteria (TSC) as established by the American Institute of Certified Public Accountants (AICPA):
- Security. Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to meet its objectives.
- Availability. Information and systems are available for operation and use to meet the entity’s objectives.
- Processing integrity. System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.
- Confidentiality. Information designated as confidential is protected to meet the entity’s objectives.
- Privacy. Personal information is collected, used, retained, disclosed, and disposed to meet the entity’s objectives.
As organizations have sought better ways to manage their risks from external relationships, they’re beginning to build requirements for SOC 2 reporting directly into their service organization contracts to support due diligence and establish a monitoring mechanism. As a result, we’ve seen a large increase in demand for SOC 2 reports. In our experience, they now comprise approximately one-half of all third-party assurance reports requested by service organizations.
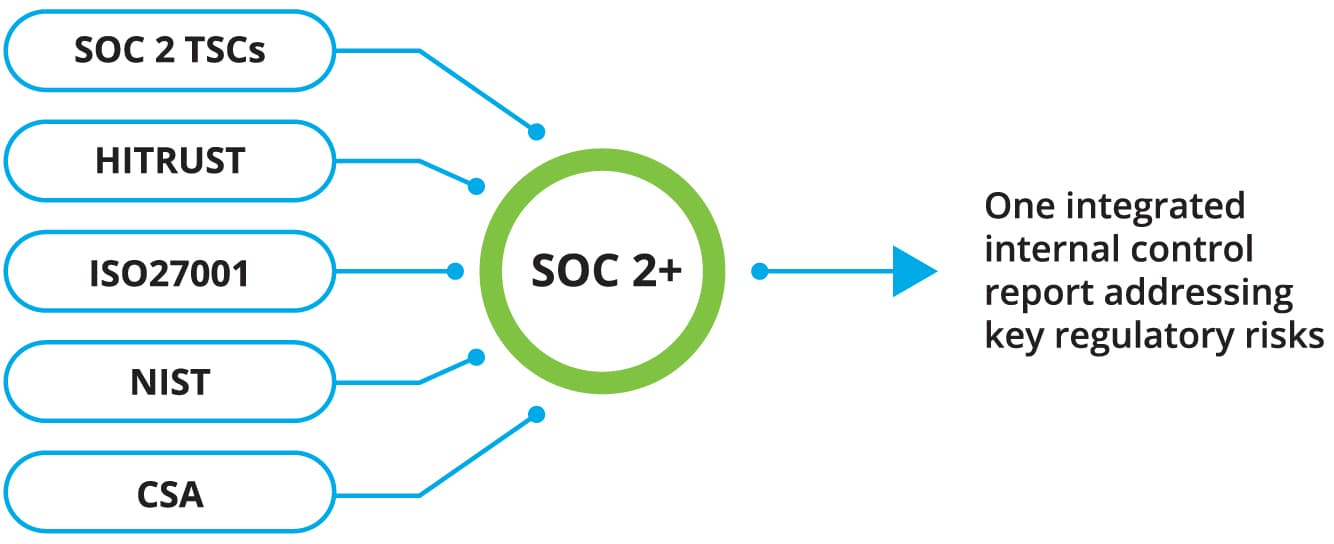
Enhanced SOC 2 reports, also called SOC 2+ reports, are in demand. These reports are being used to demonstrate assurance in areas that go beyond the TSC, including compliance with a wide range of regulatory and industry frameworks, such as those sponsored by the National Institute of Standards and Technology (NIST) and the International Standardization Organization (ISO), among others (see figure 1).
Figure 1. SOC 2: Entering a more expansive territory for reporting

SOC 2+ reports: A way for service organizations to highlight their integrated controls
Providing assurance about the TSC may be sufficient for some service organizations’ customers. But others may require greater detail. In particular, those in industries such as health care and financial services have additional industry-specific regulations and requirements. Therefore, the AICPA created SOC 2+. It’s an extensible framework that allows service auditors to incorporate various industry standards into a SOC 2 report. This integrated approach has been rapidly embraced by service organizations and their customers.
SOC 2+ reports are highly flexible tools that can incorporate multiple frameworks and industry standards into third-party assurance reporting (see figure 2). This flexibility can create substantial efficiencies for service organization customers, including reducing the amount of resources required for third-party oversight. Because SOC 2+ reports are based on a common control framework and address various industry standards, organizations generally don’t have to spend as much time and effort conducting performance reviews at their service organizations.
Organizations, as well as their service organizations, are also less likely to be exposed to compliance violations that can result in various forms of liability, including fines. For these reasons, some organizations have begun to stipulate their preference for using integrated frameworks as a means of obtaining third-party assurance by writing it into their service organization contracts.
Though customers can benefit greatly from SOC 2+ reports, the advantages for service organizations are even more significant. Consider that these businesses often must respond annually to hundreds of individual audit requests, customer questionnaires, and requests for proposals. Many of these inquiries ask the same questions and demand assurance on overlapping controls. Throw regulatory and industry-specific requirements into the mix, and things get even more complicated and onerous.
SOC 2+ examinations can dramatically reduce this burden. By providing a standardized format for meeting a broad range of regulatory and industry control requirements, SOC 2+ reports help to eliminate the need for redundant activities and one-off responses.
Figure 2: SOC 2+ reports can incorporate multiple frameworks

Journeying from SOC 2 to SOC 2+
SOC 2+ reports call for a different way of organizing requirements and testing controls, which may take some getting used to. Yet any business that wants to become truly proficient in its approach to third-party reporting will need to consider issuing a SOC 2+ report sooner or later. Demonstrating compliance with a wide variety of frameworks within a single document simply makes more sense than approaching each request for assurance separately. To make the journey from SOC 2 to SOC 2+ easier and more effective, here are some guiding principles culled from our experience in performing SOC 2+ attestations:
Nailing down the basic SOC 2 report is an important first step. Generally, service organizations have a certain degree of leeway when it comes to designing their SOC 2 reports. In fact, most contracts are somewhat vague (i.e., they don’t specify which Trust Service Criteria, or which systems, should be tested).
With this in mind, the leading practice is to limit the initial reporting scope to a subset of systems or criteria, emphasizing those that are most important to customers. Once the organization is confident about the controls surrounding this subset, it can then branch out, mapping and testing the controls relevant to a broader range of customer needs.
In considering how to proceed, assurance with regard to the security TSC, which forms the basis of all SOC 2 reports, is a natural place to start, particularly since cybersecurity is vitally important to many customers. The most complex of the five is the privacy TSC.
However, customers are becoming more concerned with service organizations’ interactions with end users and related privacy practices. While saving privacy for last may make sense, it can’t be overlooked. Ultimately, it may need to be addressed for compliance purposes if a service organization interacts directly with end users and gathers or stores their personal information. Given the complexity of the privacy criterion, it can be wise to get help. SOC 2 privacy reports do require more effort, and service organizations often need readiness assistance to complete them.
Every customer has different requirements. While contracts may be somewhat vague concerning the specifics of SOC 2 reporting, service organizations shouldn’t assume they know what a customer is looking for without first confirming it. For example, issuing a SOC 2 report on Application A and its associated processes, when the customer really wanted Application B to be examined, will result in wasted resources and a lot of rework. These costly misunderstandings happen far too often, especially when they can be avoided through better communication and greater insight into customer needs.
For many service organizations, understanding what their customers are looking for often comes down to educating the salesforce and other customer touchpoints about SOC 2 reporting. When customer-facing personnel grasps the value of an integrated approach, they can both communicate the benefits and ask customers the right questions to help scope and define their requirements. Making the effort up front to probe customer requirements—not only the “what” but also the “why”—will both save time in the long run and build customer confidence and trust.
Many customers may be unaware that it’s possible to combine SOC 2 with other compliance initiatives when requirements overlap. This gives service organizations a great opportunity to add value by showing customers how SOC 2+ can be used to streamline reporting processes. This can be accomplished through the following steps:
- To begin, compile a list of requirements for each TSC. Then move on to a list of requirements for each of the other frameworks with which your customers must comply.
- At the beginning of the project, identify areas where similar operational controls will meet both SOC 2 and other requirements.
- Subsequently, create a master list of the integrated requirements by mapping them to one another. This allows for testing each control once and then “checking the box” for all the requirements to which it applies.
If an organization hasn’t previously considered issuing a SOC 2+ report, then most likely external or independent auditors haven’t tested its integrated compliance controls before. Also, it isn’t uncommon for service organizations, particularly those subject to Sarbanes-Oxley (SOX) Section 404, to focus their control efforts primarily on ICFR. If so, they may not have applied that same level of rigor to the controls for their operational systems.
For these reasons, a readiness assessment, performed by an independent third party, is often well worth the effort. This includes inspecting the controls that are already designed and implemented, as well as identifying any gaps that will need to be addressed prior to live testing.
A readiness assessment can ultimately save time and effort by:
- Identifying problems before they need to be reported;
- Leveraging subject matter experts to document controls; and
- Defining the correct scope and boundaries of the system up front.
In our experience, service organizations that don’t complete a readiness assessment tend to have more issues during the actual examination.
Once the necessary controls and procedures are in place for SOC 2, an organization can start integrating other frameworks. Individual controls will invariably fulfill multiple requirements. For example, a control that meets one of the requirements of a SOC 2 Security Trust Service Criteria, may also meet certain NIST and ISO 27001 security requirements. Mapping these redundancies greatly facilitates testing efficiencies when seeking to comply with multiple industry-specific or regulatory requirements.
Rapidly gaining traction
The complexity of the extended enterprise has exposed both service providers and their customers to many risks that could be difficult to mitigate. On one hand, organizations that outsource important and mission-critical functions need assurance that their providers have rigorous control processes in place. On the other hand, service organizations need a way to streamline how they provide that assurance.
SOC 2+ reports are rapidly gaining traction as the preferred method of addressing these concerns because they provide an efficient approach to organizing, testing, and reporting on controls for multiple frameworks simultaneously. Service organizations that use SOC 2+ reports adeptly may gain a competitive advantage over other providers that are less proficient in their approaches to third-party reporting. And perhaps best of all, by using SOC 2+ reports to facilitate information exchange, everybody wins—as members of the extended enterprise gain the insight needed to better manage risk together.

Are you looking for help with critical business issues and anticipating risk?
Discover our Third-Party Assurance Services
Get in touch
Sara Lademan |
Dan Zychinski |
Alan West |
Recommendations
Vigilant threat studies
Insights for better threat management and response

