Reinforce resilience.
Realize opportunities.
Disrupt your disruptors.
Deloitte's Cyber & Strategic Risk services offer a unified approach to help you tackle obstacles and build new capabilities fast. Leverage our breadth and depth of solutions to transform your organization and secure your success, wherever you are on your journey.
What are your greatest challenges?
The stakes are high for addressing increasingly complex cyber and risk challenges, but with Deloitte, you can overcome your greatest hurdles and achieve your strategic goals. Together, we’ll quickly develop a plan and course of action, whether you need help with strategy, design, implementation, or ongoing operations. Navigate your most critical paths, realize salient outcomes, and position your organization to thrive.
Overview
Amid today’s complex threat environment, your ability to stay ahead of adversaries, design for resilience, and create secure working environments is paramount. By effectively protecting the enterprise, you’ll reduce disruption and enable productivity.
Priority outcomes we can help you achieve
Secure, connected devices
Unleash innovative use cases at the edge—without sacrificing security. Operate in distributed, modern environments while protecting a variety of traditional and nontraditional endpoints powered by next-generation networks and technologies, such as 5G, IoT, and edge computing.
Learn more
Secure, intelligent operations
Experience the difference an enhanced security posture makes in the face of threats and disruptions. Forge a better balance between intel-driven prevention and battle-tested response to reach greater operational efficiency.
Learn more
Secure, efficient workforce experience
Provide a secure and frictionless experience for employees and contractors across applications and networks. Leverage the latest innovations and techniques in identity and access management, application security, and data protection to achieve greater collaboration, agility, and resilience in the face of threats.
Learn more
Overview
Consistently securing cross-channel experiences has become critical, as ways of engaging stakeholders (customers, vendors, and other third parties) and business models have gone digital. Effectively manage the incredible amounts of data that digital technologies generate to promote responsible data use and protection of privacy.
Priority outcomes we can help you achieve
Trusted customer experiences
Strengthen brand and customer relationships through greater visibility and control of customer interactions—physically and digitally. Help customers control their identities and data while promoting reliable quality and security across digital engagement channels.
Learn more
Trusted data use
Improve trust by creating transparency around application and data use. Utilize a unified approach to achieve greater visibility and control over how data is collected, aggregated, used, analyzed, and protected.
Learn more
Overview
Enable your agility goals, with security and risk incorporated as a core program within your organization, rather than an obstacle to overcome. Implement agile modernization projects, such as cloud migrations or new DevOps practices, and collaborate with alliances effectively by employing supply chain security and risk-transformation initiatives.
Priority outcomes we can help you achieve
Agile, secure modernization
Manage threats to your organization’s technology landscape, and drive security and risk considerations early in the digital transformation process. Agilely develop and maintain applications and cloud environments that are secure by design, to enable game-changing business transformation.
Learn more
Supply chain security and risk transformation
Mitigate threats while maintaining operations and improving product quality and security for customers. Drive business outcomes by increasing the efficiency of procurement processes, performance of vendor relationships, and visibility into supply chains and Nth-party relationships.
Learn more
Overview
Today’s increasingly connected marketplace brings with it growing threats, making well-designed systems, processes, and strategies essential for resilience. Effectively manage a variety of security, technical, geopolitical, and financial risks, so that you can confidently react and operate in times of crisis and uncertainty.
Priority outcomes we can help you achieve
Dynamic risk programs
Proactively and more effectively manage risk, compliance, and crisis scenarios to increase confidence in decision-making, achieve strategic performance objectives, and become resilient in the face of disruption.
Learn more
Resilient digital operations
Building resilience requires shifting from a reactive to proactive operational mindset. Strike the balance between defending the business and staying agile, to meet the demands of an ever-expanding, digitally connected world.
Learn more
Enhanced response and recovery
Respond swiftly and effectively to natural disasters and high-impact events. Communicate with internal and external stakeholders, manage multiple complex workstreams, execute crisis response runbooks, and improve crisis programs to instill greater confidence and trust.
Learn more
Overview
Efficiently manage security, governance, and resource programs in the present, while preparing for disruptions and next-generation technologies. Quantum and blockchain, for example, can act as both threats and opportunities.
Priority outcomes we can help you achieve
Future forward readiness
Next-generation technologies and emerging market trends often pose threats of disruption alongside opportunities for competitive advantage. Establish future-ready strategies and roadmaps to prepare for the challenges ahead and position for strategic growth.
Learn more
Governance and optimization
Create and enhance programs that showcase the return on investment of security and risk investments. Strengthen the management and governance of your cyber and risk program today, while building for tomorrow.
Learn more
- Protect the Enterprise
- Build and Restore Trust
- Spearhead Business Enablement
- Manage Multifaceted Risk
- Provide Vision and Drive Growth
Back
Overview
Amid today’s complex threat environment, your ability to stay ahead of adversaries, design for resilience, and create secure working environments is paramount. By effectively protecting the enterprise, you’ll reduce disruption and enable productivity.
Priority outcomes we can help you achieve
Secure, connected devices
Unleash innovative use cases at the edge—without sacrificing security. Operate in distributed, modern environments while protecting a variety of traditional and nontraditional endpoints powered by next-generation networks and technologies, such as 5G, IoT, and edge computing.
Learn more
Secure, intelligent operations
Experience the difference an enhanced security posture makes in the face of threats and disruptions. Forge a better balance between intel-driven prevention and battle-tested response to reach greater operational efficiency.
Learn more
Secure, efficient workforce experience
Provide a secure and frictionless experience for employees and contractors across applications and networks. Leverage the latest innovations and techniques in identity and access management, application security, and data protection to achieve greater collaboration, agility, and resilience in the face of threats.
Learn more
Overview
Consistently securing cross-channel experiences has become critical, as ways of engaging stakeholders (customers, vendors, and other third parties) and business models have gone digital. Effectively manage the incredible amounts of data that digital technologies generate to promote responsible data use and protection of privacy.
Priority outcomes we can help you achieve
Trusted customer experiences
Strengthen brand and customer relationships through greater visibility and control of customer interactions—physically and digitally. Help customers control their identities and data while promoting reliable quality and security across digital engagement channels.
Learn more
Trusted data use
Improve trust by creating transparency around application and data use. Utilize a unified approach to achieve greater visibility and control over how data is collected, aggregated, used, analyzed, and protected.
Learn more
Overview
Enable your agility goals, with security and risk incorporated as a core program within your organization, rather than an obstacle to overcome. Implement agile modernization projects, such as cloud migrations or new DevOps practices, and collaborate with alliances effectively by employing supply chain security and risk-transformation initiatives.
Priority outcomes we can help you achieve
Agile, secure modernization
Manage threats to your organization’s technology landscape, and drive security and risk considerations early in the digital transformation process. Agilely develop and maintain applications and cloud environments that are secure by design, to enable game-changing business transformation.
Learn more
Supply chain security and risk transformation
Mitigate threats while maintaining operations and improving product quality and security for customers. Drive business outcomes by increasing the efficiency of procurement processes, performance of vendor relationships, and visibility into supply chains and Nth-party relationships.
Learn more
Overview
Today’s increasingly connected marketplace brings with it growing threats, making well-designed systems, processes, and strategies essential for resilience. Effectively manage a variety of security, technical, geopolitical, and financial risks, so that you can confidently react and operate in times of crisis and uncertainty.
Priority outcomes we can help you achieve
Dynamic risk programs
Proactively and more effectively manage risk, compliance, and crisis scenarios to increase confidence in decision-making, achieve strategic performance objectives, and become resilient in the face of disruption.
Learn more
Resilient digital operations
Building resilience requires shifting from a reactive to proactive operational mindset. Strike the balance between defending the business and staying agile, to meet the demands of an ever-expanding, digitally connected world.
Learn more
Enhanced response and recovery
Respond swiftly and effectively to natural disasters and high-impact events. Communicate with internal and external stakeholders, manage multiple complex workstreams, execute crisis response runbooks, and improve crisis programs to instill greater confidence and trust.
Learn more
Overview
Efficiently manage security, governance, and resource programs in the present, while preparing for disruptions and next-generation technologies. Quantum and blockchain, for example, can act as both threats and opportunities.
Priority outcomes we can help you achieve
Future forward readiness
Next-generation technologies and emerging market trends often pose threats of disruption alongside opportunities for competitive advantage. Establish future-ready strategies and roadmaps to prepare for the challenges ahead and position for strategic growth.
Learn more
Governance and optimization
Create and enhance programs that showcase the return on investment of security and risk investments. Strengthen the management and governance of your cyber and risk program today, while building for tomorrow.
Learn more
Strengthen cyber, strengthen the business
Cyber is much more than data, systems, and networks security. No longer relegated to a supporting role, cyber teams are emerging as players in their own right, becoming critical enablers for business transformation.
Deloitte's Cyber mission is to make the digital world a trusted and safe place where organizations can drive forward with speed and confidence. A robust cyber program enables organizations to do three things: inspire customer trust and success; build safer and better products; and help business move forward securely, decisively, and in compliance with regulations.
Solutions
Risk is ubiquitous—so we advise, implement, and operate across an extensive range of services and solutions
In a connected and open world, enterprise needs to enable trusted identities. We provide the methodologies and the platform implementation/operation solutions that will help your organization manage which employees, partners, suppliers, customers, and citizens get access to your sensitive applications and data.
Our capabilities include:
- Identity strategy, governance, and administration
- Access and advanced authentication
- Directory services
- Cloud and hosted identity solutions
- Identity analytics
- Emerging identity solutions (biometric, behavioral analytics, blockchain, AI, RPA, others)
- Identity operations and managed services
Featured solutions
Identity solutions Digital IdentityEnterprise applications are essential to your operations—so are their resilience and security. To minimize your vulnerabilities, Deloitte integrates cybersecurity and compliance activities throughout the software development life cycle (SDLC) with solutions to advise, design, build, deploy, and operate secure applications.
Our capabilities include:
- Concept and requirements
- Design and development
- Verification and authentication
- Production
- Maintenance and retirement
- DevSecOps
How can you navigate uncertainty with confidence? Strengthen your strategy to address the increasingly sophisticated risks facing your enterprise today. Deloitte designs and implements transformational enterprise security programs, organizational constructs, and capabilities so that you can better manage cyber risks aligned with business priorities.
Our capabilities include:
- Cyber assessments, frameworks, and benchmarking
- Cyber strategy and program transformation
- Cyber metrics, reporting, and risk quantification
- Cyber awareness, board reporting, and training
- Integrated risk management/governance, risk management, and compliance
- Third-party cyber risk
- Insider threat programs
Featured solutions
Cyber Strategy solutions Risk Quantification PRISM™As technology revolutionizes how we do business—and threats to operations become increasingly complex—organizations need to transform how they secure their enterprise. We provide solutions to assess, strategize, architect, implement, and operate next-gen technologies, helping you limit your risks and exposure.
Our capabilities include:
- Core infrastructure security
- Cloud infrastructure security
- Attack surface management
- Zero Trust
- Technology asset management
- Mobile and endpoint security
- Technical resilience
Featured solutions
Attack Surface Management Managed Secure Access Service Edge (MSASE) by Deloitte Zero Trust by DeloitteIn today’s complex threat environment, organizations need to stay resilient and well ahead of adversaries. Deloitte offers advanced solutions to proactively monitor, detect, and respond to the toughest cyber threats, providing expertise that you don’t have to hire and manage yourself.
Our capabilities include:
- Cyber incident hunting, detection, and response
- Managed and hybrid operate security services
- Advising and implementing solutions
- Cyber threat intelligence and analytics
- Security operations development
Featured solutions
Detect & Respond solutions Managed Extended Detection and Response (MXDR) by DeloitteSafeguarding confidential information is key to an organization’s success. We advance data privacy across the lifecycle, building sustainable, scalable programs designed around strategic principles that holistically address operational and regulatory requirements.
Our capabilities include:
- Strategy
- Program Design & Operations
- Data Privacy
- Data Protection
- Trust & Safety
- Product Compliance
- Compliance Engineering
- Risk & Controls
- Technology Implementation
Learn more
Data & Digital Trust solutions Trust by Design: A Path to Inclusive, Compliant, Safe ProductsA protected enterprise calls for cloud-security solutions that keep pace with an ever-changing threat environment. We offer a distinct vision for securing your cloud environments through the lenses of business risk, regulatory, technology, and cyber, providing implementation and operation services for a broad set of cloud transformation solutions.
Our capabilities include:
- Application modernization and migration
- Cloud security policy orchestration and automation
- Cyber cloud managed services
- Secure landing zones
- DevSecOps
- Cloud security analytics
Featured solutions
Cloud Security Management by DeloitteAs emerging technologies transform your enterprise, it’s vital to evolve how you protect it, too. Leverage our cutting-edge capabilities to navigate the potential risks and opportunities unfolding in the ever-evolving cyber and strategic risk landscape, with services to implement and operate many key solutions.
Our capabilities include:
- Internet of Things
- Secure supply chain
- 5G, advanced connectivity, and edge cyber
- Quantum
- Blockchain and digital assets
- Metaverse
Today’s organizations don’t operate in isolation. You rely on an intricate array of third-party relationships that extend your physical and virtual boundaries. Whether they’re outsourcers, alliances, suppliers, or partners, we’ll help you evaluate and manage their potential third-party risks—from identifying gaps in your defense and optimizing IT costs, to enhancing the performance of the extended enterprise and moving you closer to your strategic business goals.
Our capabilities include:
- Risk transformation
- Cost and revenue recovery
The worst that can happen sometimes does. An organization’s strength rests on how they respond. How can you anticipate, avoid, and recover from potential crises? With a collaborative platform of leading-edge tools and insights, we’ll help you become more resilient to crises and risks that can cause them.
Our capabilities include:
- Crisis response
- Crisis recovery
- Resilience
Featured solutions
Crisis management solutionsWhen it comes to reputation, perception is reality. Your brand deserves the vigilance that allows you to sense threats, shape perceptions, and measure outcomes. In today’s constantly shifting winds, we’re here to help you manage risk, achieve business objectives, and reduce threats by analyzing and addressing multiple points of vulnerability. We not only provide insights on trends and disruptors that could impact your competitive advantage, we go a step further, sharing opportunities to enhance and protect your brand for long-term performance.
Our capabilities include:
- Enterprise risk management
- Brand and reputation risk
- Brand operations solutions
Featured solutions
Brand and reputation managementSolutions
Risk is ubiquitous—so we advise, implement, and operate across an extensive range of services and solutions
- Identity
- Application Security
- Strategy
- Infrastructure
- Detect & Respond
- Data & Digital Trust
- Cloud
- Emerging Technology
In a connected and open world, enterprise needs to enable trusted identities. We provide the methodologies and the platform implementation/operation solutions that will help your organization manage which employees, partners, suppliers, customers, and citizens get access to your sensitive applications and data.
Our capabilities include:
- Identity strategy, governance, and administration
- Access and advanced authentication
- Directory services
- Cloud and hosted identity solutions
- Identity analytics
- Emerging identity solutions (biometric, behavioral analytics, blockchain, AI, RPA, others)
- Identity operations and managed services
Featured solutions
Identity solutions Customer Identity & Access Management Digital IdentityEnterprise applications are essential to your operations—so are their resilience and security. To minimize your vulnerabilities, Deloitte integrates cybersecurity and compliance activities throughout the software development life cycle (SDLC) with solutions to advise, design, build, deploy, and operate secure applications.
Our capabilities include:
- Concept and requirements
- Design and development
- Verification and authentication
- Production
- Maintenance and retirement
- DevSecOps
How can you navigate uncertainty with confidence? Strengthen your strategy to address the increasingly sophisticated risks facing your enterprise today. Deloitte designs and implements transformational enterprise security programs, organizational constructs, and capabilities so that you can better manage cyber risks aligned with business priorities.
Our capabilities include:
- Cyber assessments, frameworks, and benchmarking
- Cyber strategy and program transformation
- Cyber metrics, reporting, and risk quantification
- Cyber awareness, board reporting, and training
- Integrated risk management/governance, risk management, and compliance
- Third-party cyber risk
- Insider threat programs
Featured solutions
Cyber Strategy solutions Risk Quantification PRISM™As technology revolutionizes how we do business—and threats to operations become increasingly complex—organizations need to transform how they secure their enterprise. We provide solutions to assess, strategize, architect, implement, and operate next-gen technologies, helping you limit your risks and exposure.
Our capabilities include:
- Core infrastructure security
- Cloud infrastructure security
- Attack surface management
- Zero Trust
- Technology asset management
- Mobile and endpoint security
- Technical resilience
In today’s complex threat environment, organizations need to stay resilient and well ahead of adversaries. Deloitte offers advanced solutions to proactively monitor, detect, and respond to the toughest cyber threats, providing expertise that you don’t have to hire and manage yourself.
Our capabilities include:
- Cyber incident hunting, detection, and response
- Managed and hybrid operate security services
- Advising and implementing solutions
- Cyber threat intelligence and analytics
- Security operations development
Featured solutions
Detect & Respond solutions Managed Extended Detection and Response (MXDR) by DeloitteSafeguarding confidential information is key to an organization’s success. We advance data privacy across the lifecycle, building sustainable, scalable programs designed around strategic principles that holistically address operational and regulatory requirements.
Our capabilities include:
- Strategy
- Program Design & Operations
- Data Privacy
- Data Protection
- Trust & Safety
- Product Compliance
- Compliance Engineering
- Risk & Controls
- Technology Implementation
Learn more
Data & Digital Trust solutions Trust by Design: A Path to Inclusive, Compliant, Safe ProductsA protected enterprise calls for cloud-security solutions that keep pace with an ever-changing threat environment. We offer a distinct vision for securing your cloud environments through the lenses of business risk, regulatory, technology, and cyber, providing implementation and operation services for a broad set of cloud transformation solutions.
Our capabilities include:
- Application modernization and migration
- Cloud security policy orchestration and automation
- Cyber cloud managed services
- Secure landing zones
- DevSecOps
- Cloud security analytics
Featured solutions
Cloud Security Management by DeloitteAs emerging technologies transform your enterprise, it’s vital to evolve how you protect it, too. Leverage our cutting-edge capabilities to navigate the potential risks and opportunities unfolding in the ever-evolving cyber and strategic risk landscape, with services to implement and operate many key solutions.
Our capabilities include:
- Internet of Things
- Secure supply chain
- 5G, advanced connectivity, and edge cyber
- Quantum
- Blockchain and digital assets
- Metaverse
Today’s organizations don’t operate in isolation. You rely on an intricate array of third-party relationships that extend your physical and virtual boundaries. Whether they’re outsourcers, alliances, suppliers, or partners, we’ll help you evaluate and manage their potential third-party risks—from identifying gaps in your defense and optimizing IT costs, to enhancing the performance of the extended enterprise and moving you closer to your strategic business goals.
Our capabilities include:
- Risk transformation
- Cost and revenue recovery
The worst that can happen sometimes does. An organization’s strength rests on how they respond. How can you anticipate, avoid, and recover from potential crises? With a collaborative platform of leading-edge tools and insights, we’ll help you become more resilient to crises and risks that can cause them.
Our capabilities include:
- Crisis response
- Crisis recovery
- Resilience
Featured solutions
Crisis management solutionsWhen it comes to reputation, perception is reality. Your brand deserves the vigilance that allows you to sense threats, shape perceptions, and measure outcomes. In today’s constantly shifting winds, we’re here to help you manage risk, achieve business objectives, and reduce threats by analyzing and addressing multiple points of vulnerability. We not only provide insights on trends and disruptors that could impact your competitive advantage, we go a step further, sharing opportunities to enhance and protect your brand for long-term performance.
Our capabilities include:
- Enterprise risk management
- Brand and reputation risk
- Brand operations solutions
Featured solutions
Brand and reputation managementIndustries
- Consumer
- Energy, Resources & Industrials
- Financial Services
- Government & Public Sector
- Life Sciences & Health Care
- Technology, Media & Telecommunications
Accolades

Deloitte ranked #1 globally in Security Consulting by Gartner
Deloitte named a leader in Worldwide Managed Cloud Security Services by IDC
Deloitte recognized as a global leader in Strategic Risk Management Consulting by ALM
Deloitte named a worldwide leader in Managed Detection and Response Services by IDC
INSIGHTS

The CISO Brief
Insights for future-focused cybersecurity leaders
Deloitte’s new monthly series curated by CISOs for CISOs. Whether you’re an aspiring cyber leader or looking to expand your role, explore essential strategies, tools, and leadership skills to help you navigate these rapidly changing times.
Learn more
Tech Trends 2025
Deloitte’s 16th Annual Tech Trends report
In Deloitte’s 16th annual Tech Trends report, AI is the common thread of nearly every trend. Moving forward, it will be part of the substructure of everything we do.
Read the report

Deloitte x Snyk
Scaling AppSec for GenAI
AI is driving a rapid evolution of the technology landscape, causing AI-driven development to outpace typical AppSec program capabilities. Deloitte and Snyk discuss how to prepare your AppSec program for a world with GenAI at our fingertips.
Read the report
Perspectives
Software engineering for your digital business future
Four models of digital product engineering organizations.
Learn More

Annual Cyber Threat Trends Report 2024
Insights, emerging threats, and their potential impact
Our report illuminates some common threat vectors and provides profiles on the top hacking groups you may come across
Learn More

CISO’S Guide to Generative AI
Opportunities, outcomes, and the urgency of now
GenAI can help reinforce organizations against breaches, address talent shortages, and develop roadmaps for threat detection and response. Explore the capabilities of GenAI to bolster your cybersecurity posture.
LEARN MORE
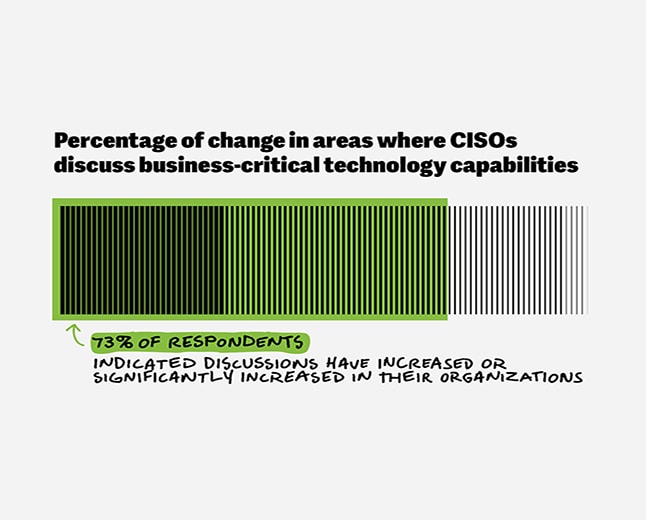
CISOs’ rising role
Shaping the Future of Cyber
Discover how the Chief Information Security Officer is evolving into a pivotal strategic leader. Learn about their enhanced responsibilities and the critical role they play in in business-critical technology conversations.
View Insights
 Previous
Previous
 Next
Next
Discover breakthrough innovation workshop centers, including CyberSphere, Greenhouses, and our Smart Factory for manufacturers, to help you tackle your most pressing challenges.
Contact us to start planning your customized risk solutions
Get in touch


US Cyber Cross-Business Integrations Leader
Principal
shchand@deloitte.com +1 773 294 6430
US Cyber Platforms & Solutions Leader
Principal
vkunchala@deloitte.com +1 713 982 2807
US Cyber Innovation & Marketing Leader
Principal
dmapgaonkar@deloitte.com +1 408 704 4481
US Cyber Ecosystems & Alliances Leader
Principal
anmorrison@deloitte.com +1 404 220 1170

Explore our job openings in Cyber & Strategic Risk
Insert Custom HTML fragment. Do not delete! This box/component contains code
that is needed on this page. This message will not be visible when page is
activated.
+++ DO NOT USE THIS FRAGMENT WITHOUT EXPLICIT APPROVAL FROM THE CREATIVE
STUDIO DEVELOPMENT TEAM +++
Insert Custom HTML fragment. Do not delete! This box/component contains code
that is needed on this page. This message will not be visible when page is
activated.
+++ DO NOT USE THIS FRAGMENT WITHOUT EXPLICIT APPROVAL FROM THE CREATIVE
STUDIO DEVELOPMENT TEAM +++